What are CIS Benchmarks?
The CIS Benchmarks cover a collection of recommended hardening policies specifying different hosts, applications, and operating systems that include detailed recommendations on system configuration, security settings, and other measures that can help organizations safeguard their IT infrastructure against a wide range of cyber threats.
The benchmarks cover various platforms and technologies such as operating systems, cloud environments, databases, web browsers, and mobile devices.
There are a number of actions you need to perform to use CIS Benchmark recommendations to make sure that your servers are hardened:
- Setting name – which contains the actual recommendation, and the level (L1) that classifies the importance of the recommendation. A recommendation can be classified either as L1- mandatory recommendation, L2 – recommendations that can be implemented at a later stage of the hardening project, and NA- which will be the last one in its importance due to the specific configuration dependencies.
- Profile Applicability – which system component will be affected by this policy.
- Description – a description of the setting’s rule.
- Rationale – The rationale behind setting the rule the way it is recommended.
- Impact – any expected impact on your production.
- Audit – audit recommendations for this rule.
- Remediation – ways you can enforce this rule on your machine.
- Default value – The default value of the setting as it set ‘out of the box’.
- References – a reference to the relevant CCE
- CIS Controls – the relevant CIS Controls that this policy is related to.
How to Use CIS Benchmark Recommendations
Implementing the CIS Benchmarks is a big step towards achieving a hardened infrastructure, but also one of the most complicated ones.
There are a number of actions you need to perform in order to make sure that your servers are hardened:
1.) When beginning your server hardening project, the first thing you should do is define a structured baseline based on industry best practices such as the CIS benchmarks or DISA STIG's
2.) Applying security patches: Regularly update your servers with the latest security patches to address vulnerabilities and protect against known exploits.
3.) Implementing strong access controls: Enforce strong authentication mechanisms, such as complex passwords or multifactor authentication, to prevent unauthorized access to your servers.
4.) Regular reviews of User Rights Assignment settings are essential to ensure that access privileges are current and aligned with organizational requirements and security best practices
5.) Disabling unnecessary services: Disable any unnecessary services or protocols on your servers to minimize potential attack vectors.
6.) Use automated configuration monitoring that can check all remotely-testable secure configuration elements, and raise alerts if unauthorized changes occur (new listening ports, new admin users, changes in the group and local policy objects, and new services running on the system). Tools that integrate with Security Content Automated Protocol are (SCAP) recommended.
7.) Deploy system configuration management tools that will automatically enforce system configuration settings - periodically, or preferably, in real-time. Using them, you should be able to redeploy or have real-time control over the configuration settings on a scheduled, manual, or event-driven basis.
As with such complex tasks, difficulties often arise and production systems are often harmed. In order to establish a configuration recommendation, lab testing should be performed before implementing the change in production. These tests require long hours of testing for every change to be made in the system. As the enterprise's network constantly changes, keeping track of the baseline hardening status and implementing CIS benchmark hardening is almost impossible to perform without hitches.
How Benchmarks are Developed
CIS Benchmarks are developed through a unique consensus-based process led by a group of IT Experts and Cybersecurity Professionals and subject matter experts from around the world, each of which continuously identifies, refines and validates security best practices within their areas of expertise. There are more than 12,000 professionals in the CIS Benchmark Communities collaborating on one benchmark.
When a CIS Benchmark is being developed, it goes through 2 phases of consensus review.
Phase One
The first phase and the initial development of a benchmark begins with defining the scope which initiates the discussion for a benchmark to be reviewed. After scope is determined the CIS team creates the first draft of the CIS benchmark. By using the CIS WorkBench community forum, the subject matter experts will then deliberate until a consensus can be reached. Once the drafts have been finalized and a consensus has been reached among the CIS community, the final CIS Benchmark is then published and released online.
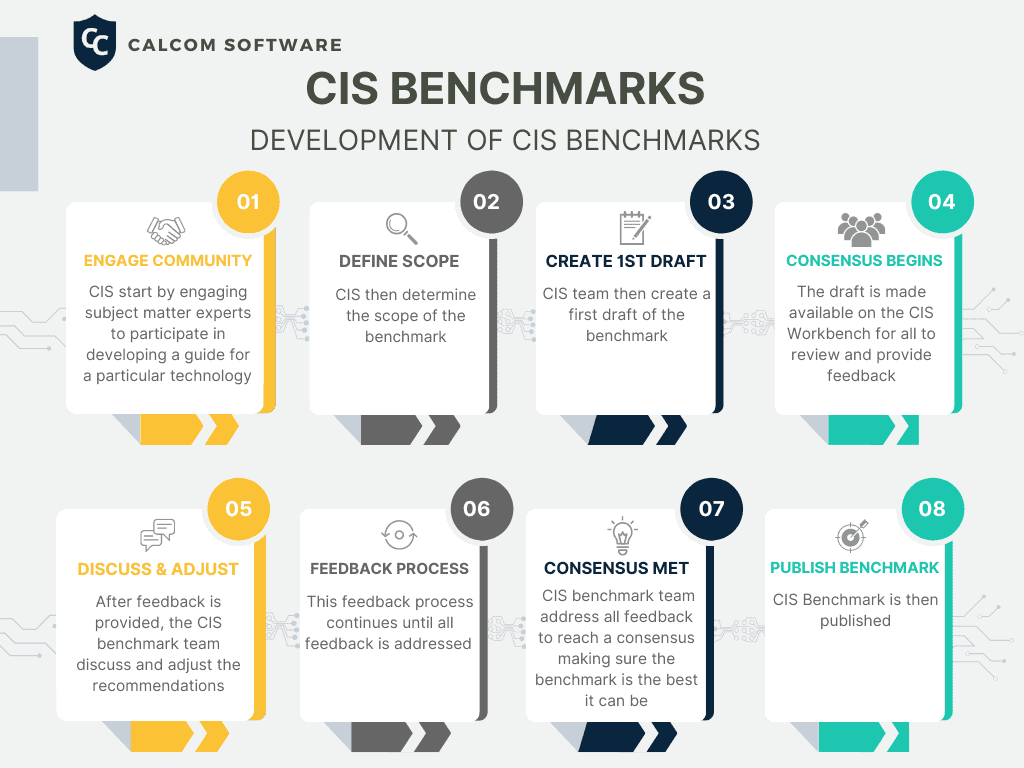
Infographic: Development of CIS Benchmarks
Phase Two
In phase two after the benchmark has been published, the consensus team reviews the feedback from the internet second community for incorporation into the benchmark.
Explanation of the CIS Benchmarks Levels
Most of the CIS Benchmarks include multiple configuration profiles that describe the configurations assigned to a benchmark's recommendation. These levels are known as Level 1, Level 2, and STIG Profile which replaced Level 3. Every recommendation within each CIS Benchmark is associated with at least one level profile.
CIS Level 1 profile recommends essential basic security requirements that can be implemented on any system with little or no performance impact or reduced functionality. Intent of Level 1 is to reduce the attack surface while allowing machines to remain operational and not hindering the businesses functionality.
CIS Level 2 profile recommends more stringent security settings and is considered to be "defense in depth" and is intended for environments where security is paramount. Recommendations associated to Level 2 can cause a reduction in functionality of a system and have adverse effects if not properly implemented.
STIG Profile (Level 3 replacement) recommends security configurations specific to STIG. Overlap of recommendations from other profiles, i.e. Level 1 and Level 2, are present in the STIG profile as applicable.
CIS Benchmark Categories
There are eight technology categories also known as the CIS Benchmark List that the Benchmarks can be categorized in.
The 8 Benchmark Categories are:
Operating System Benchmarks
Operating System Benchmarks provide instructions for securely configuring various operating systems such as Microsoft Windows, Linux, Apple OSX, and others. They cover a wide range of security-related settings, including access management, driver installation and browser configurations.
Server Software Benchmarks
Server Software Benchmarks provide configuration baselines and recommendations for server settings, server admin controls, storage settings and secure configuration of Microsoft Windows Server, Kubernetes, SQL Server, and other server software.
Cloud Infrastructure and Services Benchmarks
Cloud Infrastructure and Services Benchmarks provide security best practices and standards for cloud infrastructures such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform. The guidelines include best practices for virtual network settings, identity and access management, logging, regulatory compliance, security controls and more.
Mobile Device Benchmarks
Mobile Device Benchmarks provide security configurations for operating systems that run on mobile phones, tablets, and other hand-held devices. Best practices include developer settings, app permissions, privacy settings and more.
Network Device Benchmark
Network Device Benchmark describes how to securely configure network devices such as firewalls, routers, switches, and virtual private networks (VPNs). Guidance is provided for both vendor-neutral and vendor specific recommendations to ensure secure setup and management of these network devices.
Desktop Software Benchmarks
Desktop Software Benchmarks cover most desktop software organizations typically use. Guidelines include best practices for managing desktop software features such as browser settings, access privileges, user accounts, mobile device management (MDM) and more.
Multi-Function Print Devices Benchmark
Multi-Function Print Devices Benchmark cover secure configuration best practices for multi-functional printers such as firmware updates, wireless network access, file sharing settings and more.
DevSecOps Tools Benchmark
DevSecOps Tools Benchmarks provides prescriptive guidance for establishing a secure configuration posture for securing the Software Supply Chain.
CIS Assessment
To effectively evaluate and enhance cybersecurity measures, we will delve into various CIS assessment tools designed to identify vulnerabilities, measure compliance, and strengthen overall security posture.
Scanners and Assessment Tools
This group of tools will indicate your CIS Benchmark compliance and security posture. Using them will indicate the gap between your current policy and the CIS Benchmarks. They will not provide any solution for overcoming this gap, and you will have to test and enforce the changes to improve your compliance posture. The CIS offers its own developed scanner – the CIS CAT.
Configuration Management Tools
Configuration management tools are not necessarily specific for security purposes, but they allow the implementation of configuration changes on your infrastructure. These tools are relevant only after you scanned and found the gap between your policy and the CIS Benchmark and tested the predicted impact of each configuration change. Examples of this kind of tool are Chef, Ansible, and Tripwire Configuration Manager.
Hardening Automation Tools
Hardening automation tools basically provide a comprehensive solution for server hardening. They do everything from scanning, through implementing and also monitoring and maintaining the compliance and security posture. Their biggest advantage is that they eliminate the need to check what will be the impact of each configuration change on your network. This is by far the most painful, time and resources consuming part of hardening. Hardening automation tools offer the following solution:
- Scanning and discovering the gap between your current policy and your desired policy.
- Learning your network and indicating what will be the impact of each configuration change.
- Implement the new policy directly on production without testing or breaking anything.
- Monitoring, controlling, and preventing configuration changes, all from a single point of control.
CIS Workbench Explained
CIS relies on the WorkBench Communities to help with the development, revision and editing of the CIS Benchmarks to maintain their recommended secure configurations. The Communities also help with the creation and security best practices of the CIS Critical Security Controls (CIS Controls).
The CIS Workbench was created as the official home for these communities to come together and collaborate on the Benchmarks consensus process and best practices of the CIS Controls. Discussions range from a spectrum of topics such as intricate technical configuration settings to overarching cybersecurity policies. By bringing together these groups on a unified platform, it enables a comprehensive understanding of crucial initiatives, such as the correlation between content in the CIS Benchmarks and Safeguards outlined in the CIS Controls.
CIS WorkBench simplifies engagement in multiple communities through its user-friendly dashboard. It provides an effortless way to track discussion topics and monitor the progress of CIS Benchmarks during the approval process. Users can easily create tickets, navigate group forums, and access publicly-available resources for CIS Controls and CIS Benchmarks through the platform.
Benchmarks in Additional Formats
Benchmarks are available for free download in PDF format. Get CIS Benchmarks.
CIS SecureSuite Members have the added benefit of accessing CIS Benchmarks in various formats through the CIS WorkBench, including Word, Excel, XML, and more.
Frequency of Benchmark Releases
The release of new CIS Benchmarks vary depending on the release schedule of the technology the benchmark supports and the Benchmark Community. However, as of March 2023 all CIS Windows Server and Windows Workstation Benchmarks will be updated once a year to align with Microsoft's update schedule. CIS will release major version updates (i.e., updating from v1.12.0 to v2.0.0) to account for significant changes in the operating system.
The CIS Windows Benchmarks are regularly updated to include the latest Windows build version within 90 days of its release. Regardless of the version being used, they are designed to be used with all build person up to the most recent version to save time when searching for a specific build number of a CIS Windows Benchmark.
Benefits of CIS Benchmarks for Comprehensive Security Best Practices
As delivered from the manufacturer, the operating systems’ default configuration is aimed at usability, rather than security. Thereby, without taking measures to secure it, operating systems are highly vulnerable to cyber-attacks.
Regulations should also be taken into consideration when deciding whether or not to use CIS Benchmarks. It is fair to say that almost all the major regulations require CIS Benchmark compliance directly or indirectly. And by indirectly we mean that some regulations require compliance to other frameworks, such as NIST Cybersecurity Framework, but these frameworks refer to the CIS Benchmarks.
|
PCI-DSS |
CIS Benchmarks |
|
HIPAA |
CIS Benchmarks |
|
CMMC |
CIS Benchmarks |
|
ISO 27001 |
NIST |
|
23 NYCRR Part 500 |
NIST |
PCI-DSS (Payment Card Industry Data Security Standard) and CIS Benchmarks: While they have different focuses, they can be complementary. PCI-DSS is a set of security standards specifically designed for protecting cardholder data, while CIS Benchmarks provide guidelines for secure system configuration across different platforms. Organizations handling payment card data may use CIS Benchmarks as a reference for implementing secure configurations to meet PCI-DSS requirements.
HIPAA (Health Insurance Portability and Accountability Act) and CIS Benchmarks: HIPAA is a US regulation that sets standards for protecting sensitive patient health information. CIS Benchmarks, on the other hand, provide security recommendations for various technologies. Organizations in the healthcare sector can refer to CIS Benchmarks to enhance their security posture and align with HIPAA requirements.
CMMC (Cybersecurity Maturity Model Certification) and CIS Benchmarks: CMMC is a framework established by the US Department of Defense to assess and enhance the cybersecurity posture of organizations in the defense supply chain. CIS Benchmarks can be used as a resource to implement specific security controls and best practices aligned with CMMC requirements.
ISO 27001 (International Organization for Standardization) and NIST (National Institute of Standards and Technology): Both ISO 27001 and NIST provide frameworks for information security management. ISO 27001 is an international standard that outlines requirements for establishing, implementing, maintaining, and continually improving an information security management system (ISMS). NIST provides a comprehensive set of guidelines, controls, and best practices for various aspects of cybersecurity. While ISO 27001 is a standard, NIST documents, such as the NIST Special Publication 800 series, offer detailed guidance that can be used to support ISO 27001 implementation.
23 NYCRR Part 500 and NIST: 23 NYCRR Part 500 is a regulation issued by the New York State Department of Financial Services (NYDFS) that establishes cybersecurity requirements for financial institutions operating in New York. NIST provides a framework and guidelines for cybersecurity that can be used by organizations to meet the requirements of 23 NYCRR Part 500. NYDFS specifically references NIST as a recognized industry standard in their regulation.
MITRE ATT&CK framework is a comprehensive knowledge base that describes various tactics, techniques, and procedures (TTPs) commonly employed by threat actors during cyber attacks. Its purpose is to provide organizations with a standardized framework for understanding and categorizing adversary behaviors.





