What are CIS Controls?
The Center for Internet Security (CIS) Controls are a prioritized set of Safeguards to mitigate the most common cyber-attacks against systems and networks. The SANS 20 Critical Security Controls, formerly known as the SANS Top 20, is now called the CIS Controls and has been reduced to 18 Controls since version 8.
You may be wondering, How many CIS Controls are there? There are 18 CIS Controls overarching measures that Information Security teams in organizations of all sizes can implement to protect their systems and data in order to be CIS compliant.
Government agencies ensure that hardware and software adhere to stringent standards, ensuring controls work effectively to safeguard sensitive information. The CIS Controls are mapped to and referenced by multiple legal, regulatory, and policy frameworks.
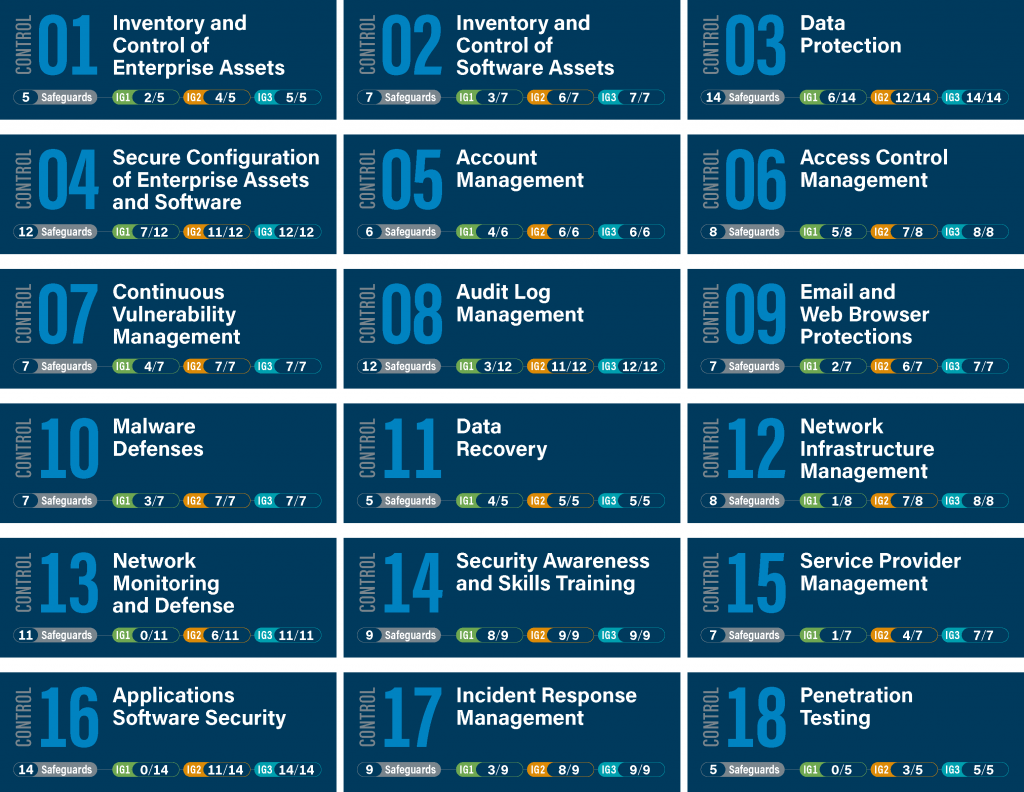
The 18 CIS Controls v8 are:
Breakdown and Explanation of the 18 CIS Controls v8
Understanding critical security controls for effective cyber defense is the starting point for building a resilient and proactive cybersecurity strategy. This breakdown will provide a comprehensive understanding of the technical foundations and practical applications of the CIS Controls for CIS Compliance:
- CIS Control 1: Inventory and Control of Enterprise Assets: Actively manage (inventory, track, and correct) all hardware devices on the network so that only authorized devices are given access, and unauthorized and unmanaged devices are found and prevented from gaining access.
- CIS Control 2: Inventory and Control of Software Assets: Actively manage (inventory, track, and correct) all software on the network so that only authorized software is installed and can execute, and that unauthorized and unmanaged software is found and prevented from installation or execution.
- CIS Control 3: Data Protection: Establish and maintain an inventory of data that needs to be protected (e.g., PII, PHI), classify it based on its level of sensitivity, and ensure it is appropriately secured.
- CIS Control 4: Secure Configuration of Enterprise Assets and Software: Establish, implement, and actively manage (track, report on, correct) the security configuration of enterprise assets using a rigorous configuration management and change control process in order to prevent attackers from exploiting vulnerable services and settings.
- CIS Control 5: Account Management: Control access to systems and applications based on the principle of least privilege; limit unnecessary access to sensitive data; restrict access to critical systems; ensure that accounts are assigned only to authorized users; ensure that accounts are disabled when no longer needed or when an employee leaves the organization.
- CIS Control 6: Access Control Management: Ensure that only authorized users have access to systems and applications based on their assigned job functions; ensure that users have only the necessary privileges to perform their job functions; monitor user activity for unauthorized actions.
- CIS Control 7: Continuous Vulnerability Management: Continuously acquire, assess, and take action on new information in order to identify vulnerabilities, remediate them in a timely manner, and minimize the window of opportunity for attackers.
- CIS Control 8: Audit Log Management: Collect audit logs from all systems and networking components; store logs securely; review logs regularly for signs of suspicious activity; retain logs for an appropriate amount of time.
- CIS Control 9: Email and Web Browser Protections: Protect email systems against phishing attacks by implementing technical controls such as email filtering; protect web browsers against malicious code by implementing technical controls such as web filtering.
- CIS Control 10: Malware Defenses: Protect against malware by implementing technical controls such as antivirus software; establish policies for handling malware incidents.
- CIS Control 11: Data Recovery: Ensure that data can be recovered in the event of a data loss incident by implementing technical controls such as backups; test backups regularly.
- CIS Control 12: Network Infrastructure Management: Manage network infrastructure devices such as routers, switches, firewalls, etc., using rigorous configuration management and change control processes in order to prevent attackers from exploiting vulnerable services and settings.
- CIS Control 13: Network Monitoring and Defense: Monitor networks for signs of suspicious activity; respond promptly to incidents; establish policies for handling incidents.
- CIS Control 14: Security Awareness and Skills Training: Train employees on how to recognize phishing attacks; establish policies for reporting suspicious activity.
- CIS Control 15: Service Provider Management: Ensure that third-party service providers are held accountable for meeting security requirements; establish policies for handling incidents involving third-party service providers.
- CIS Control 16: Application Software Security: Ensure that application software is developed securely by following secure coding practices; test applications regularly for security vulnerabilities.
- CIS Control 17: Incident Response Management: Establish an incident response plan that includes procedures for detecting incidents, responding to incidents, reporting incidents to appropriate parties (e.g., law enforcement), recovering from incidents, conducting post-incident reviews.
- CIS Control 18: Penetration Testing: Conduct regular penetration testing exercises in order to identify vulnerabilities before attackers do; conduct red team exercises in order to test the effectiveness of security controls; conduct incident response tabletop exercises in order to test the effectiveness of incident response plans.
CIS Controls vs CIS Benchmarks
The CIS Controls and CIS Benchmarks can cause a bit of confusion. Here is a simple explanation:
CIS Controls are a general set of recommended best practices for securing a wide range of systems and devices and are referenced throughout the CIS Benchmarks.
CIS Benchmarks are guidelines that provide actionable best practices for specific platforms and technologies for hardening specific operating systems, middleware, software applications, and network devices.
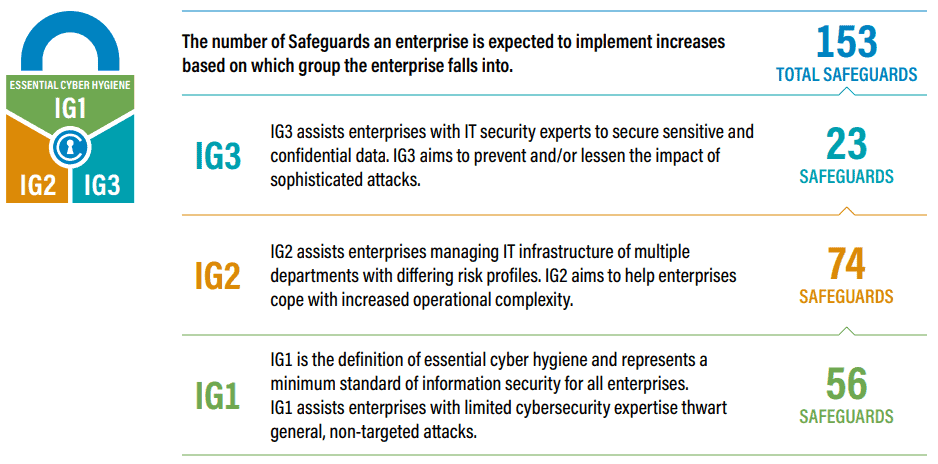
CIS Control Safeguards
There are a total of 153 Safeguards in CIS Controls v8 which are prioritized into Implementation Groups (IGs). Every enterprise should start with IG1. IG1 is defined as "essential cyber hygiene," the foundational set of cyber defense Safeguards that every enterprise should apply to guard against the most common attacks
"Safeguards" were known as "Sub-Controls" prior to Version 8 of the CIS Controls.
Source: CIS Implementation Groups
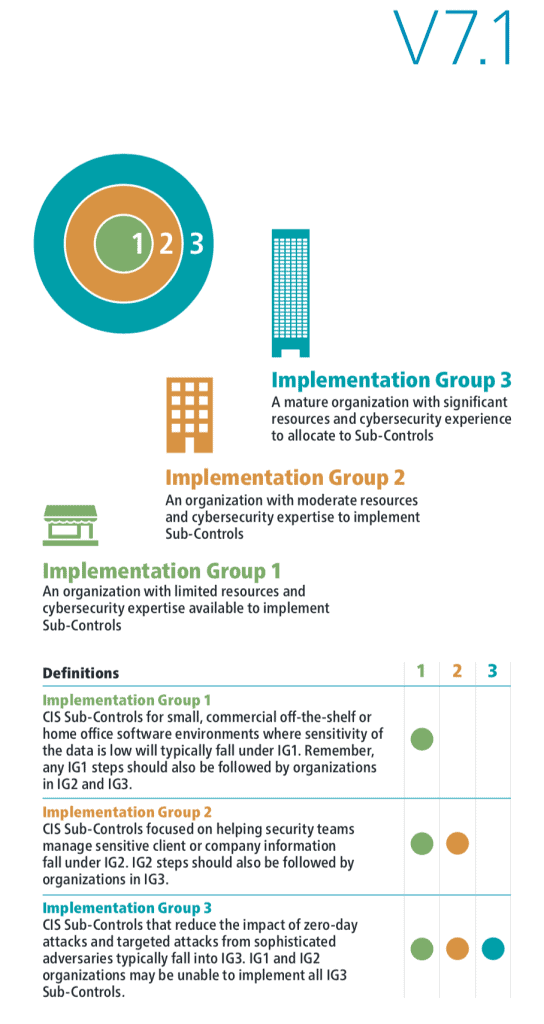
Explaining CIS Implementation Groups (IGs)
CIS Controls Implementation Groups (IGs) provide guidance on how to prioritize implementation. The IGs are self-assessed categories for organizations based on relevant cybersecurity attributes. Each IG identifies a subset of the CIS Control standards that are identified to be applicable for an enterprise with a similar risk profile and resources to strive to implement. These IGs represent a horizontal look across the CIS Controls tailored to different types of enterprises.
Essential Cyber Hygiene is defined as IG1 the foundational set of cyber defense Safeguards that every enterprise should apply to guard against the most common attacks. Each IG then builds upon the previous one: IG2 includes IG1, and IG3 includes all CIS Safeguards in IG1 and IG2.
Source: CIS Implementation Group
CIS Community Defense Model
CIS released the Community Defense Model (CDM), which is a data-driven approach to identifying the usefulness of specific CIS Control recommendations. The CDM looks at the conclusions of recent Verizon Data Breach Investigations Report (DBIR), along with data from the Multi-State Information Sharing and Analysis Center (MS-ISAC), to identify what CIS believes to be the five most important types of attacks.
CIS describes those attacks using the MITRE Adversarial Tactics, Techniques, and Common Knowledge (MITRE ATT&CK) Framework in order to create attack patterns (or specific combinations of Tactics and Techniques used in those attacks). This allows CIS to analyze the value of individual defensive actions (i.e., Safeguards) against those attacks. It also provides a consistent and explainable way to look at the security value of a given set of defensive actions across the attacker's life cycle and provides a basis for strategies like defense-in-depth.
The following attack patterns are included within the CDM:
- Web-Application Hacking
- Insider and Privilege Misuse
- Malware
- Ransomware
- Targeted Intrusions
These are presented in order of priority based on data from the Verizon DBIR.
Why CIS Controls are Important for System Hardening
System hardening involves implementing security measures to reduce vulnerabilities and protect against potential threats. CIS Controls play a vital role in system hardening by offering organizations a structured and effective approach to increase their cybersecurity defenses, and the CIS Controls provide a comprehensive framework to achieve this goal.
The Controls are developed based on real-world attack data and insights from cybersecurity experts. This means they are rooted in practical experiences and reflect the evolving threat landscape, making them highly relevant and applicable to organizations across various industries.
Implementing the CIS Controls is essential for system hardening. Learn more about how CalCom's Hardening Automation Suite can help you increase your security posture.
Learn about the Implementation Groups and essential cyber hygiene with this downloadable poster from CIS.