RDS: Do not allow clipboard redirection
Hardening the “RDS: Do not allow clipboard redirection” settings is a fundamental step in server hardening. Hardening servers can be a painful procedure. Hardening remote services such as RDS is one of the most critical operational components when hardening servers as it have immediate impact on user and application functionality. Endless hours, and resources are invested in this process. However, despite the efforts, hardening often causes damage to production server environments. In fact, over 60% of IT professionals report they’ve experienced downtime while trying to harden their infrastructure.
After years of hardening using the traditional manual tools, we concluded that using hardening automation tools is essential for achieving a successful hardening project and a good server compliance posture with CIS benchmarks and other. Learn more about server hardening automation.
This article aims to provide basic information regarding the RDS Clipboard Redirection setting, which enables the copy paste function in remote desktop. This setting have the potential to create significant negative impact on production servers and applications. Once you’ll decide this setting’s desired value, make sure you test it, to fully understand what will be its impact on your production.
What is Clipboard Redirection
The "Do not allow Clipboard redirection" setting specifies whether to prevent the sharing of clipboard contents (clipboard redirection) between a remote computer and a client computer during a Remote Desktop Services session. By disabling this setting you won’t be able to initiate a copy – paste action in a remote desktop (RDS) session.
You can use this setting to prevent users from redirecting clipboard data to and from the remote computer and the local computer.
*If the status is set to Enabled, users cannot redirect clipboard data.
*When Disabled, Remote Desktop Services always allows clipboard redirection (this is the default behavior).
*If the status is set to Not Configured, clipboard redirection is not specified at the Group Policy level. However, an administrator can still disable clipboard redirection using the Remote Desktop Session Host Configuration tool.
Potential Vulnerability for Clipboard Redirection:
Microsoft's clipboard sharing channel supports several data formats such as CF_HDROP, which is responsible for the "Copy & Paste" feature. When used, it allows us to simply copy a group of files from one computer to the other. If the client itself fails to prevent malicious files from entering his computer via this feature, he could be vulnerable to a path traversal attack. The server can then drop malicious files in arbitrary paths on the client's computer. In other words, the client's approval of the files is the only thing protecting him from this vulnerability. Considering the fact that the client doesn't even need to verify the received files coming from the RDP server, it is almost impossible to detect the attack.
According to the MITRE ATT&CK RDP/RDS is used by many attack campaigns. The Clipboard feature of RDS is significantly critical as it imposes an attack method which is hard to detect and prevent. As stated by MITRE ATT&CK:
“Adversaries may collect data stored in the clipboard from users copying information within orbetween applications.
For example, on Windows adversaries can access clipboard data by using clip.exe or Get-Clipboard. Additionally, adversaries may monitor then replace users' clipboard with their data(e.g., Transmitted Data Manipulation).
Mitigations: This type of attack technique cannot be easily mitigated with preventive controls since it is based on the abuse of system features.”
How to Mitigate Clipboard Redirection Vulnerability:
Attackers commonly use RDP for malicious activity, therefore it is recommended to configure the Remote Desktop Server to only allow required tasks. If you've decided that some users do need the clipboard function enabled, it is recommended to segment the LANs that have RDP clipboard enabled, so they can be tracked.
The Potential Impact of Clipboard Redirection Disabling:
As simple as it sounds, remote users won't be able to use the clipboard functionality. That may lead to damage in production for applications that rely on this ability.
Vulnerability Severity:
Critical
CalCom’s RECOMMENDED VALUE:
Enable
HOW TO CONFIGURE Clipboard Redirection:
Windows Server 2022:
- Launch "gpedit.msc".
- Navigate to "Computer Configuration" > "Administrative Templates" > "Windows Components" > "Remote Desktop Services" > "Remote Desktop Session Host".
- Ensure "Do not allow Clipboard redirection" is set to "Not Configured" or "Disabled".
Windows Server 2019:
- Launch "gpedit.msc".
- Navigate to "Computer Configuration" > "Administrative Templates" > "Windows Components" > "Remote Desktop Services" > "Remote Desktop Session Host".
- Ensure "Do not allow Clipboard redirection" is set to "Not Configured" or "Disabled".
Windows Server 2016:
In Windows 2016, Group policy is controlling these settings.
- Launch "msc".
- Navigate to "Computer Configuration" > "Administrative Templates" > "Windows Components" > "Remote Desktop Services" > "Remote Desktop Session Host".
- Ensure "Do not allow Clipboard redirection" is set to "Enabled".
Windows Server 2012:
- Open "Server Manager".
- Select "Remote Desktop" Services.
- Select "Collections".
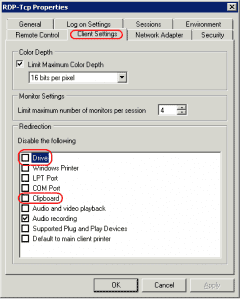
- Select "Tasks", then choose "Edit Properties".
- Under the "Client Settings" tab, ensure the "Clipboard" and "Drive" are disabled.
Windows Server 2008:
- Launch "Remote Desktop Session Host Configuration" from the server.
- Under "Connections", right-click the connection and select "Properties".
- Select the "Client Settings" tab, and make sure the "Clipboard" box is checked. If you don't want to allow copying and pasting of files, make sure the Drive selection is checked. Click OK when done.
Server Hardening Automation:
Since the testing process is complex and highly prove to human mistakes, we recommend automating the entire hardening process. CalCom offers a fully automated server hardening tool – CHS. CHS's unique ability to 'learn' your network eliminates the need to perform lab testing while ensuring zero outages to your production environment. CHS will allow you to implement your policy directly on your production servers, hassle-free.