Does Windows use LDAP?
The primary protocol employed within Microsoft’s Active Directory(AD) is Lightweight Directory Access Protocol (LDAP). While LDAP serves as a fundamental component in AD, its application extends beyond, enabling user authentication in various tools and client environments. This includes Red Hat Directory Servers on UNIX systems and OpenLDAP, an open-source application used on Windows platforms.
Leveraging LDAP’s authentication and user management functionalities can be beneficial across different domains such as API management, role-based access control (RBAC), and services like Docker and Kubernetes.
Difference between Active Directory and LDAP
Active Directory, developed by Microsoft, is a directory service tailored for Windows domain networks. It functions as a repository for data pertaining to diverse devices and resources within the network, enabling administrators to regulate permissions and control access effectively. Information in Active Directory is organized as objects along with their associated attributes.
This directory service relies on protocols such as LDAP, DNS, and Kerberos. Kerberos facilitates authentication processes, while LDAP is utilized for information retrieval. Additionally, DNS plays a crucial role in identifying Active Directory domain controllers, which are the servers responsible for hosting the Active Directory domain service.
LDAP Authentication, Configuration and Security Hardening – Signing, Binding and Configuring
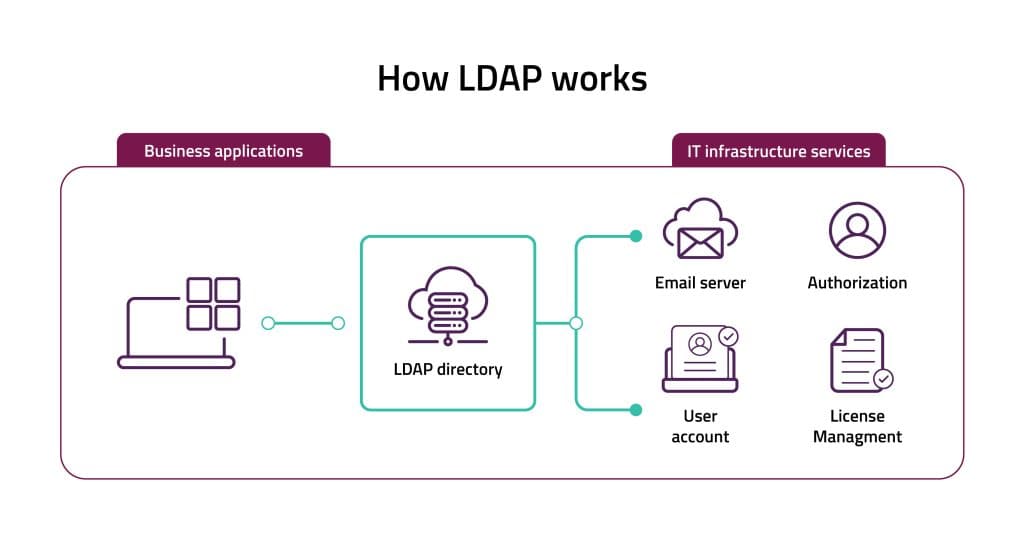
How LDAP is used in Active Directory
Lightweight Directory Access Protocol (LDAP) is a protocol used for accessing and managing directory information services, such as Active Directory (AD). Active Directory is a directory service developed by Microsoft for Windows domain networks. AD and LDAP have a complementary relationship.
Here’s how LDAP is used in Active Directory:
Authentication: When you log in to a Windows domain that uses Active Directory, LDAP is often used behind the scenes. Your login credentials are sent through LDAP to the directory service for verification against the user data stored in AD.
Directory Services: LDAP provides a structured and hierarchical way to organize and store directory information within Active Directory. It allows for the storage of information about users, groups, computers, printers, and other network resources. This information is stored in a directory tree structure called the Directory Information Tree (DIT).
Data Access: LDAP allows authorized applications to search for and retrieve specific user or group information from Active Directory. This data can be used for various purposes, such as populating user lists or enforcing access controls.
Management: While most administrators use graphical tools to manage Active Directory, LDAP can also be used to write scripts or tools to automate administrative tasks on the directory service.
Directory Replication: Active Directory uses LDAP for directory replication between domain controllers. Replication ensures that changes made to directory information on one domain controller are synchronized with other domain controllers in the network. This synchronization process helps maintain consistency and reliability within the directory service.
Group Policy: LDAP plays a role in the implementation of Group Policy in Active Directory. Group Policy Objects (GPOs) define settings and configurations for users and computers within the network. LDAP is used to retrieve GPO information and apply policy settings to appropriate users and computers based on their membership in Active Directory groups and organizational units.
Directory Integration: LDAP facilitates integration with other directory services and applications that support LDAP protocols. Active Directory can interoperate with LDAP-compliant systems, allowing for centralized management of directory services across heterogeneous environments.
Overall, LDAP serves as a critical component in the functionality and management of Active Directory, providing authentication, directory services, querying capabilities, replication, and integration with other systems.
LDAP Authentication Process
LDAP and Active Directory
Two critical LDAP configurations must be enforced in Active Directory Domain Controllers.
Domain controller: LDAP server signing requirements’ is set to ‘Require signing’
Unsigned network traffic is a good source for man-it-the-middle attacks. LDAP man-in-the-middle attacks can result in Domain Controllers making decisions that are based on false information coming from the LDAP directory. Therefore, requiring LDAP signing is crucial in Domain Controllers. Another way to improve security is to use IPsec authentication header mode to ensure mutual authentication and packet integrity for IP traffic. The default LDAP configuration does not require signing, so it is important to take active actions to prevent this high-risk vulnerability.
Note that Domain Members’ LDAP must be configured to negotiate signing or higher, or they won't be able to communicate with the Domain Controller.
You should test the potential impact of this policy before enforcing it, to make sure that there are no clients that are configured to authenticate with AD while using unsigned LDAP. Requiring signing will interfere with these applications' functions. For more information about how you can automate the testing and enforcement process, continue your reading here.
Domain controller: LDAP server channel binding token requirements’ is set to ‘Always’
Requiring Channel Binding can prevent attackers from capturing users' credentials and reusing them in another TLS session. I addition, it helps to lower the chances for man-in-the-middle attacks.
By default, no LDAP channel binding validation is performed. Changing this setting from 'Never' to 'Always' can have an impact on production.
Requiring channel binding means that all authentication request that doesn't use channel binding will be rejected. Therefore, all LDAP clients must provide information binds over SSL/TLS. Clients must have security updates under CVC-2017-8563 to support channel binding. Having channel binding without this security update installed may not be enough.
Securing Active Directory LDAP Authentication without breaking production
There are many scenarios where Active Directory’s unique LDAP configuration requirements can lead to Domain Members and applications not being able to authenticate and communicate with the Domain Controllers. It is not uncommon when security and functionality don't come in one hand.
To prevent production dysfunctions you should perform an impact analysis. The most common method for impact analysis is to first change the setting in a test environment that simulates your production. This is feasible only in infrastructures with a limited number of servers (up to 150 servers, according to our experience). Building a test environment for large and complex infrastructures is very resource-demanding. Therefore, most large organizations leave their Active Directory LDAP unhardened.
The best solution for this challenge is to automate the hardening procedure. A good hardening automation tool should generate an impact analysis report automatically, enforce your policies on your production and maintain your servers' compliance posture. A hardening automation tool is essential for minimizing the attack surface and achieving compliance at large and complex infrastructures.