Creating a safe and secure environment is a top priority for all types of organizations. To accomplish this goal, it is essential to adhere to group policy best practices, particularly in the realm of GPO security. By configuring fundamental Group Policy Settings correctly, organizations can significantly enhance their security posture. When Group Policies are utilized effectively, they play a crucial role in safeguarding users’ computers from various threats and potential breaches. In this Group Policy Guide we will cover:
What is Group Policy?
Group Policy is a feature of the Microsoft Windows NT family of operating systems that controls the working environment of user accounts and computer accounts.
In a well-structured Active Directory environment, a good Organizational Unit OU structure is essential for efficient management. By organizing users and computers into separate OUs, you can quickly identify and administer specific groups within your network. To enforce policies and settings effectively, Group Policy Objects (GPOs) can be linked at the OU level or even at the domain level.
User rights assignment can be configured through GPOs to ensure that the right individuals have the necessary permissions and privileges. Group Policy Preferences can also be utilized to fine-tune settings and preferences for users and computers, allowing for a more customized and streamlined management approach.
Group Policy Settings give centralized control to the administrator that make it easier to apply computer configurations for the admin to manage applications, operating systems, and user settings in Active Directory. Moreover, Group Policy brings forward many advantages, including efficient system management, strong password policy implementation, the configuration of folders, and file redirection.
What is Group Policy Objects (GPO) and types
When a user logs on to a domain, that domain’s Group Policy Objects are retrieved and applied to the user's system. Some examples of Group Policy Objects are:
- A GPO that force displays a specific webpage when user's in the domain opens a browser.
- A GPO that allows a shared network printer connection to the users connected on the
- A GPO can also be configured for altering settings, such as choosing default programs, preventing users from accessing the control panel, changing internet settings, and turning systems display at a certain time.
The presence of branch offices and browsing of internet websites creates multiple potential entry points for attackers to gain access to a domain By restricting internet access, hardening domain controllers, and using WMI filters to target policies to specific groups of computers, GPOs can help to prevent unauthorized access and protect against malware and other threats.
Group Policy Objects (GPOs) types
Group Policy Object have three main types to be aware of:
Local Group Policy Objects
If policy settings need to be implemented only for one Windows computer or just for one user, this is when this type of GPOs is of use. Local group policy objects exist by default on all Windows computers and are utilized when IT admins need to apply policy settings to a single Windows computer or user. These types of GPO’s only apply to local computers and to the users that log on to that computer on-site.
Non-local Group Policy Objects
Unlike local GPO’s, non-local group policy objects require your Windows computers and users to be linked to Active Directory objects, sites, domains, or organizational units. This means that non-local GPO’s can apply to one or more Windows computers and users.
Starter Group Policy Objects
Starter GPO’s are nonlocal GPO templates for group policy settings. These templates are particularly useful when creating in the Active Directory a new GPO. They enable IT administrators, to pre-configure a group of settings that represent a baseline for any future policy to be created.
GPO elevation of privilege Risk
Group Policy best practices state to limit the privilege level of users to the bare minimum and not allow a domain user to be a part of the local administrator's group. Reason being, that a local administrator can override every group policy that was applied by the domain administrator, essentially making the GPOs ineffective in enforcing settings on a corporate network. For this particular exploit, when Group Policy improperly checks access, an attacker could run processes with elevated privileges.
GPO Vulnerability
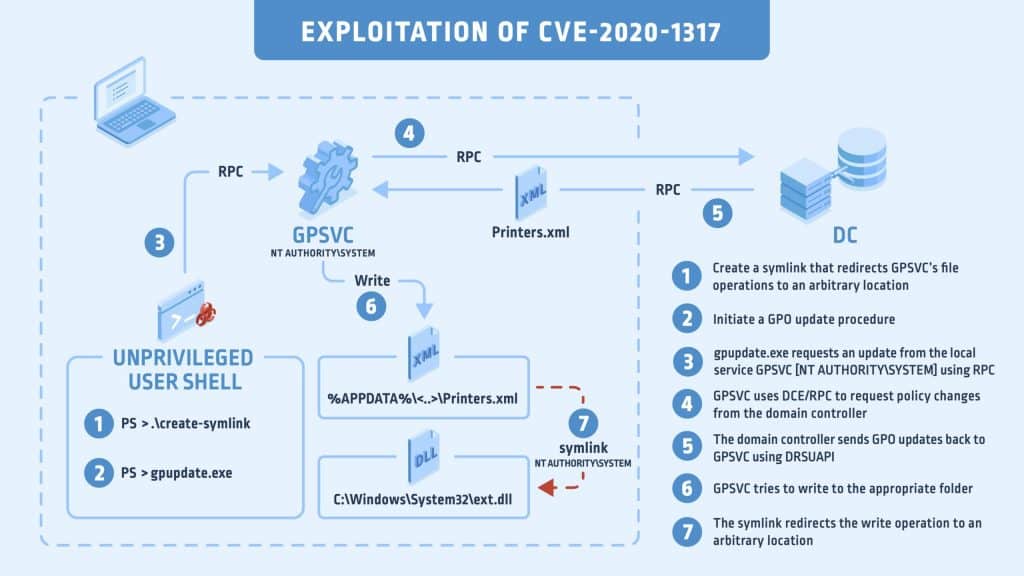
CVE-2020-1317 vulnerability permits a standard user in a domain environment to perform a file system attack allowing malicious users to evade anti-malware solutions, bypass security hardening and allow the attacker full control of the Windows systems. This vulnerability impacts any Windows machine (2008 or higher) and escalates its privileges in a domain environment.
Image credit: Shimony, Eran. (2020). Group Policies Going Rogue. CyberArk
A Remote Code Execution (RCE) vulnerability can exist if the GPO is not hardened. If the GPO fails to retrieve a valid security policy it can in turn apply a default potentially less secure group policy. RCE vulnerability can range from malware execution to an attacker gaining full control over a compromised machine.
11 Important Group Policy Settings to Prevent Breaches
To prevent breaches we have listed the top 11 most important Group Policy settings for a System Administrator. The default domain controller GPO contains predefined settings that govern the security and configuration of domain controllers in an Active Directory environment.
Domain controller server hardening reduces the attack surface available to compromise active directory security. The presence of branch offices and browsing of internet websites creates multiple potential entry points for attackers to gain access to a domain. To limit exposure, domain controller security should be a top priority.
Applying security frameworks such as the CIS Benchmark through Group Policy Objects (GPOs) locks down domain controllers to prevent unauthorized changes by compromised user accounts across Active Directory.
Be sure to apply the GPO settings to everyone in the forest and update the Group Policy Settings so that it is reflected on all the Domain Controllers in the environment.
-
-
-
-
-
-
-
- Moderating Access to Control Panel
- Control Access to Command Prompt
- Disallow Removable Media Drives, DVDs, CDs, and Floppy Drives
- Disable Guest Account
- Prevent Windows from Storing LAN Manager Hash
- Disable Forced System Restarts
- Restrict Software Installations
- Set Minimum Password Length to Higher Limits
- Set Maximum Password Age to Lower Limits
- Disable Anonymous SID Enumeration
- Disable SID/Name Translation
-
-
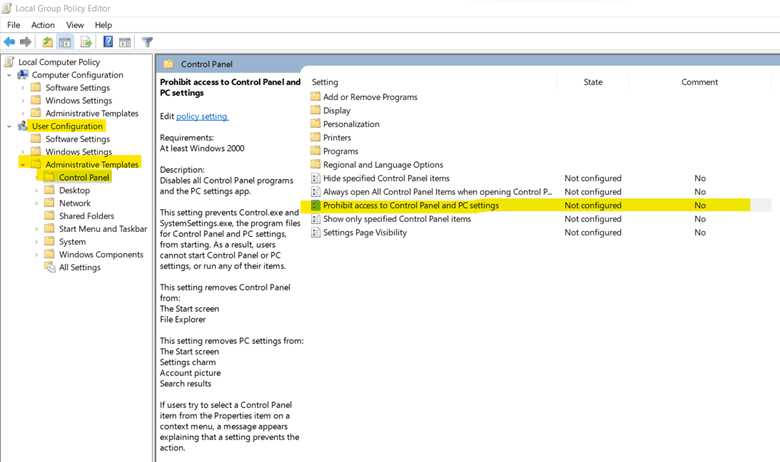
1. Moderating Access to Control Panel
Creating a GPO Setting that limits access to the computers' control panel provides a safe organizational environment. All the operations of computer are controllable via Control Panel and by moderating access to control panel, data can be made safe and unbreachable.
-
-
Steps to set this policy:
a. Open Group Policy Management Editor, you can do so by searching for Group Policy Management or by using "Windows + R" to open Run and write in it "gpedit.msc" and click "ok".
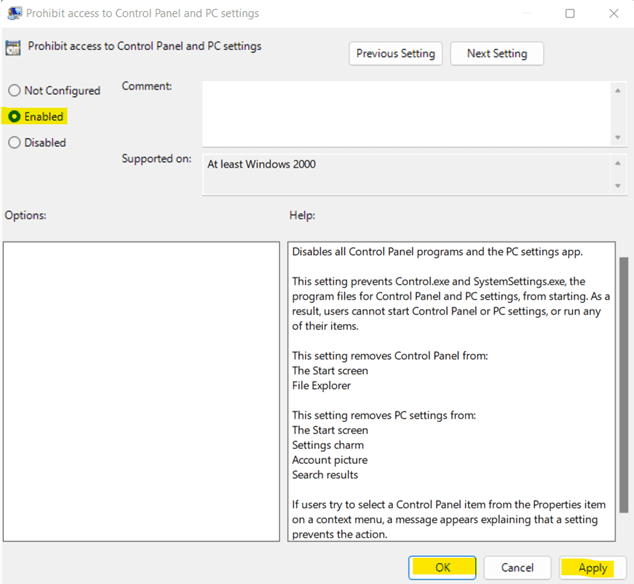
b. Under User Configuration, go to Administrative Templates -> Control Panel. Then, open Prohibit Access to Control Panel and PC settings.c. Select Enabled from the given options.
d. Click on Apply and OK. -
-
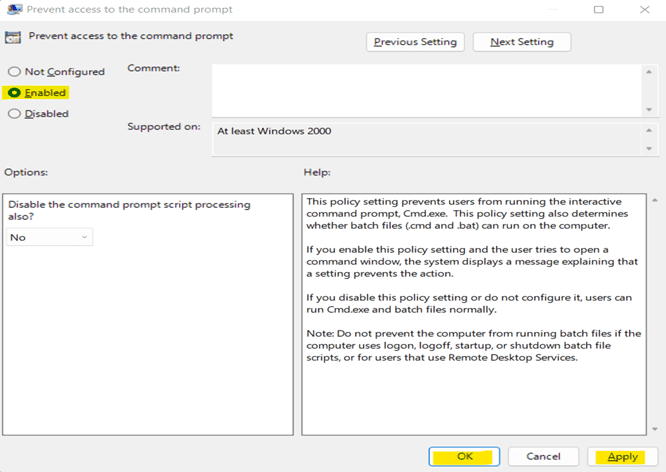
2. Control Access to Command Prompt
Controlling user access to Command Prompt (cmd.exe), to secure system resources in vital. Because with access to cmd.exe a user can pass commands to authorize high-level access to user accounts. Disabling access to cmd.exe makes the system resources secure.
Steps to set this policy:
a. Open Group Policy Management Editor, you can do so by searching for Group Policy Management or by using "Windows + R" to open Run and write in it"gpedit.msc"and click “ok”
b. Under User Configuration, go to Administrative Templates -> System. Then, open Prevent access to command prompt
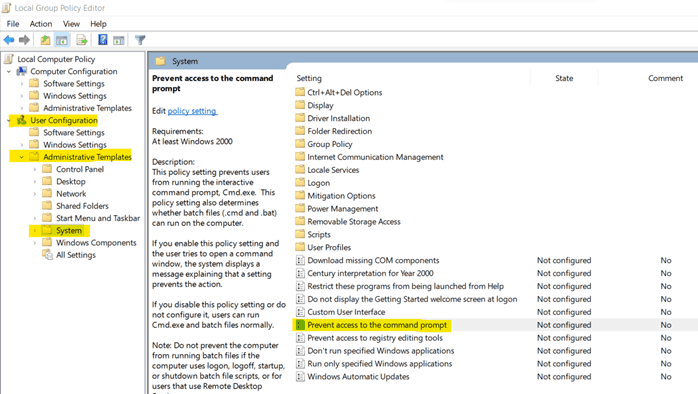
- d. Click on Apply and OK.
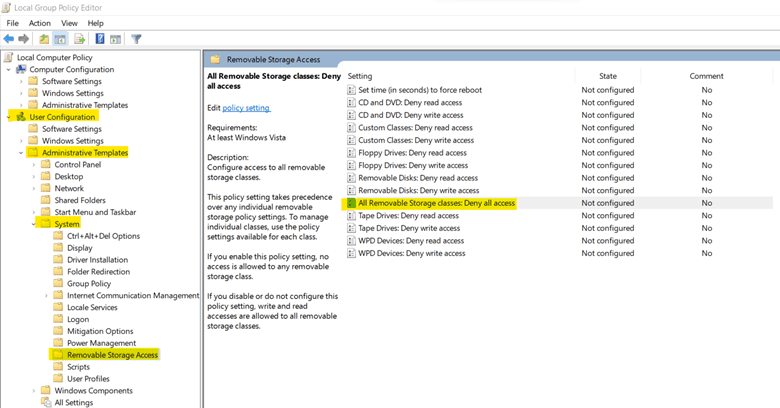
3. Disallow Removable Media Drives, DVDs, CDs, and Floppy Drives
Removable media drives are mostly defenseless so they are an easy medium for transferring viruses and malwares. So, by disallowing connection of these removable devices a system can be protected.
Steps to set this policy:
a. Open Group Policy Management Editor, you can do so by searching for Group Policy Management or by using "Windows + R" to open Run and write in it "gpedit.msc" and click "ok".
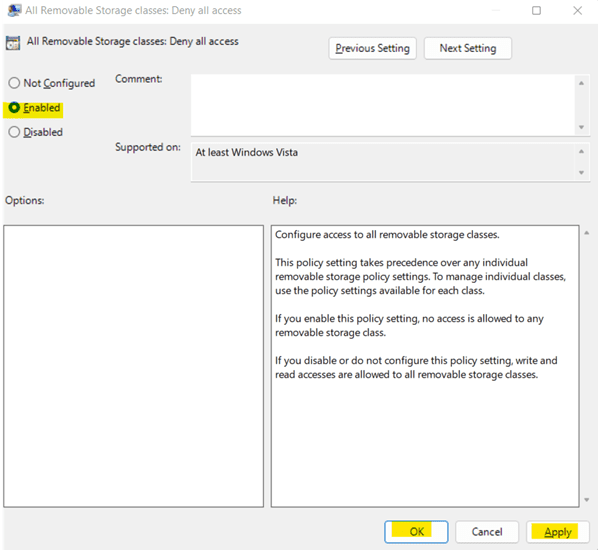
b. Under User Configuration, go to Administrative Templates -> System -> Removable Storage Access. Then, open All Removable Storage classes: Deny all access.
c. Select Enabled from the given options.
d. Click on Apply and OK.4. Disable Guest Account
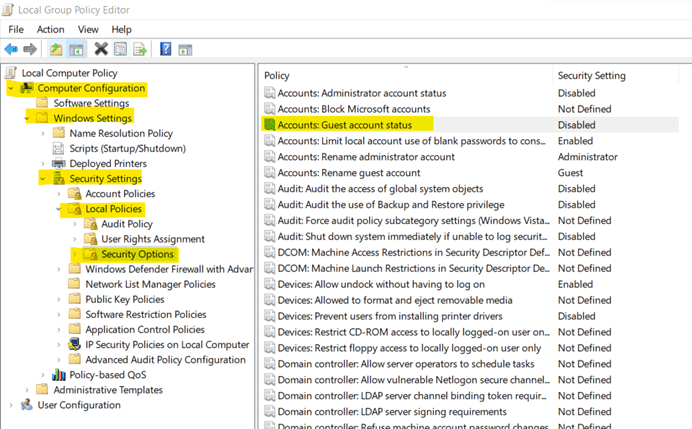
With a Guest Account a user can access Windows and a password is not required for a Guest Account. So, with this a user account can access sensitive data which can be disastrous sometimes. By default, guest accounts are disabled but checking this policy setting must be a priority.
Steps to set this policy:
a. Open Group Policy Management Editor, you can do so by searching for Group Policy Management or by using "Windows + R" to open Run and write in it "gpedit.msc" and click "ok".
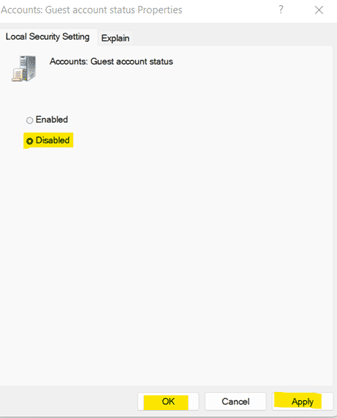
b. Under Computer Configuration, go to Windows Settings -> Security settings -> Security Options. Then, open Accounts: Guest account status.
c. Select Disabled from the given options.
d. Click on Apply and OK.
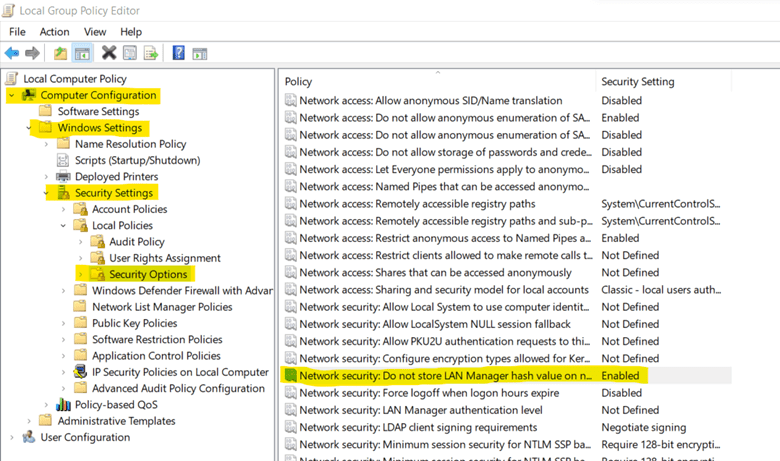
5. Prevent Windows from Storing LAN Manager Hash
User accounts credentials are generated in Windows and are stored in the Security Accounts Manager (SAM) database. Windows stores the passwords in both Lan Manager hash (LM hash) and Windows New Technology hash (NT hash). It is preferred that the passwords should not be stored in LM hash because it is a conventional and weak method and can be hacked.
Steps to set this policy:
a. Open Group Policy Management Editor, you can do so by searching for Group Policy Management or by using "Windows + R" to open Run and write in it "gpedit.msc" and click "ok".
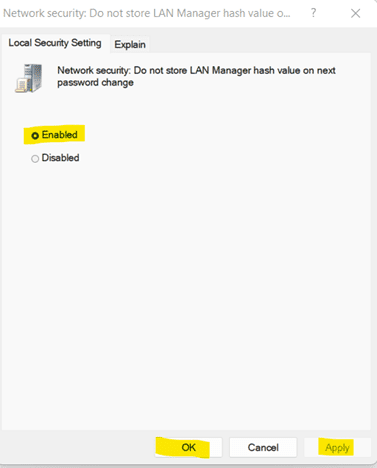
b. Under Computer Configuration, go to Windows Settings -> Security settings -> Security Options. Then, open Network Security: Do not store LAN Manager hash value on next password change.
c. Select Enabled from the given options.
d. Click on Apply and OK.6. Disable Forced System Restarts
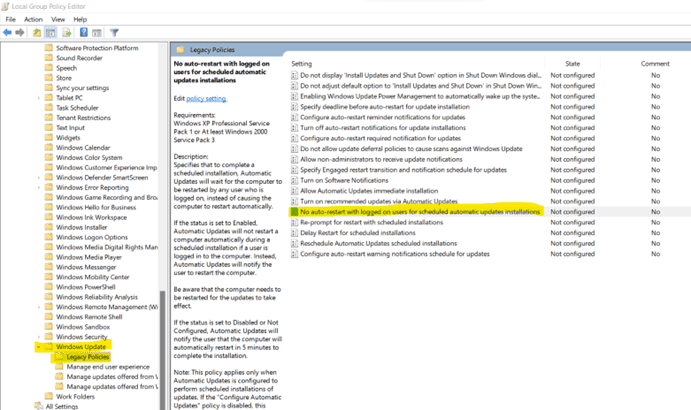
This is a common problem and needs to be solved if you don't want to lose your important unsaved work. Sometimes systems display a message that your system needs to restart because of an update and if that pop up is missed your system tends go to forced restart. So, forced system restart must be disabled.
Steps to set this policy:
a. Open Group Policy Management Editor, you can do so by searching for Group Policy Management or by using "Windows + R" to open Run and write in it "gpedit.msc" and click "ok".
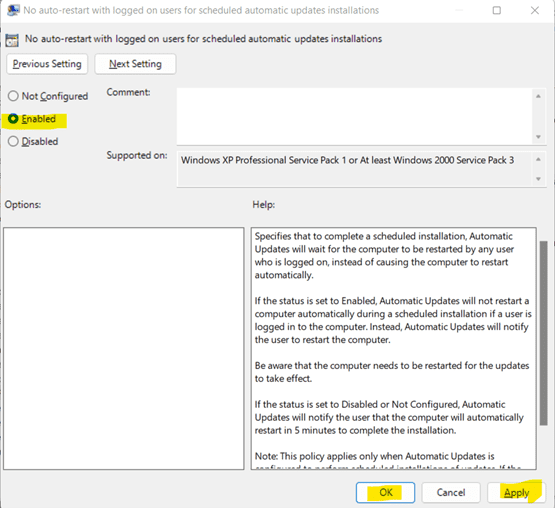
b. Under Computer Configuration, go to Administrative Templates -> Windows Component -> Windows Update -> Legacy Policies. Then, open No auto-restart with logged on users for scheduled automatic updates installation.
c. Select Enabled from the given options.
d. Click on Apply and OK.
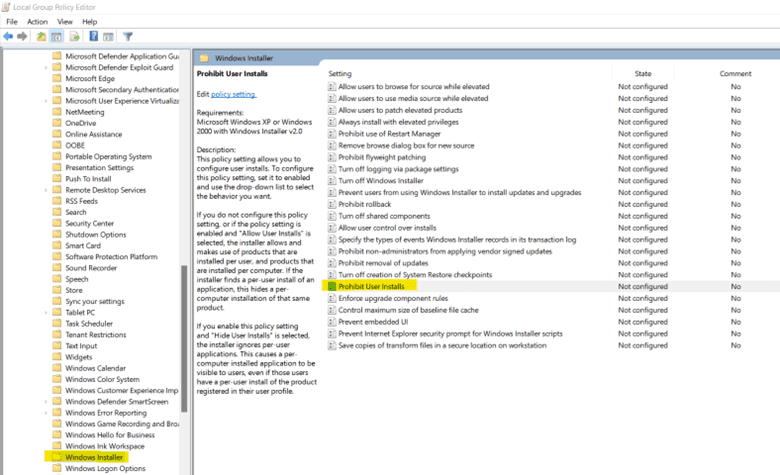
7. Restrict Software Installations
Restricting the installation of unwanted software that may compromise your system is important. If installation is allowed then the system admins have to do routine checkup of the systems. Best case solution for this is to restrict software installations via group policy.
Steps to set this policy:
a. Open Group Policy Management Editor, you can do so by searching for Group Policy Management or by using "Windows + R" to open Run and write in it "gpedit.msc" and click "ok".
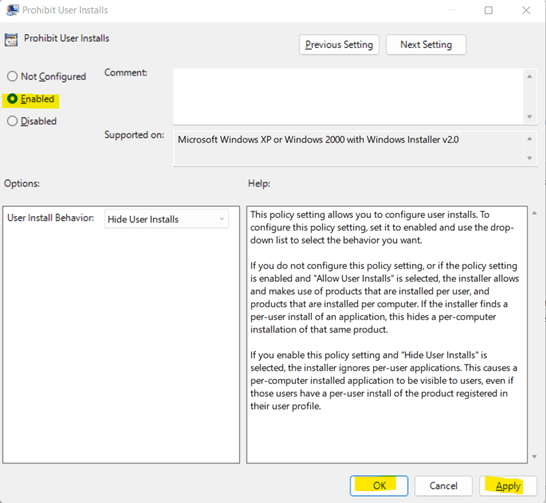
b. Under Computer Configuration, go to Administrative Templates -> Windows Component -> Windows Installer. Then, open Prohibit User Installs.
c. Select Enabled from the given options.
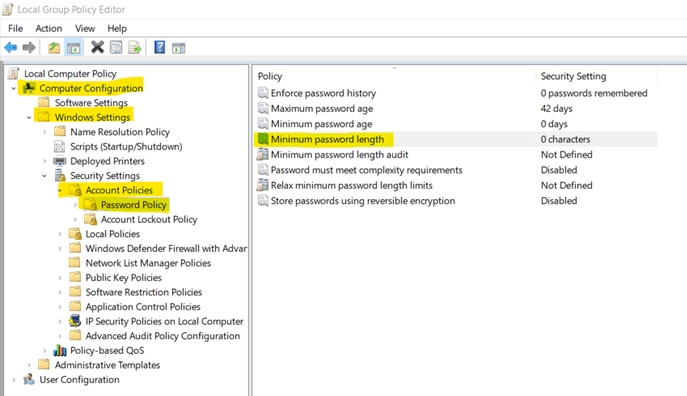
d. Click on Apply and OK.8. Set Minimum Password Lengths to Higher Limits
Setting the minimum password length to higher limits lowers unnecessary risks. By default, the value for this setting is "0". You have to specify a number in order to set minimum password length.
Steps to set this policy:
a. Open Group Policy Management Editor, you can do so by searching for Group Policy Management or by using "Windows + R" to open Run and write in it "gpedit.msc" and click "ok".
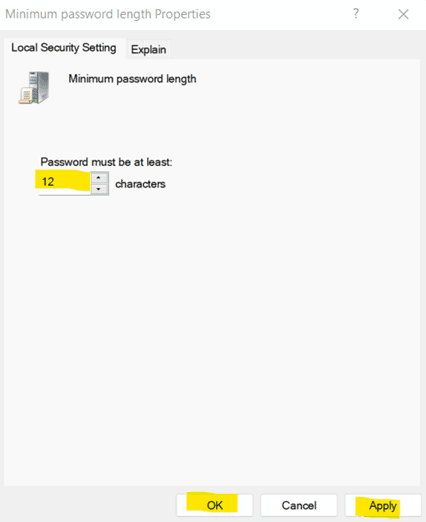
b. Under Computer Configuration, go to Windows Settings -> Security Settings -> Account Policies -> Password Policy. Then, open Minimum Password Length.
c. Enter the numeric value (preferably 12 characters).
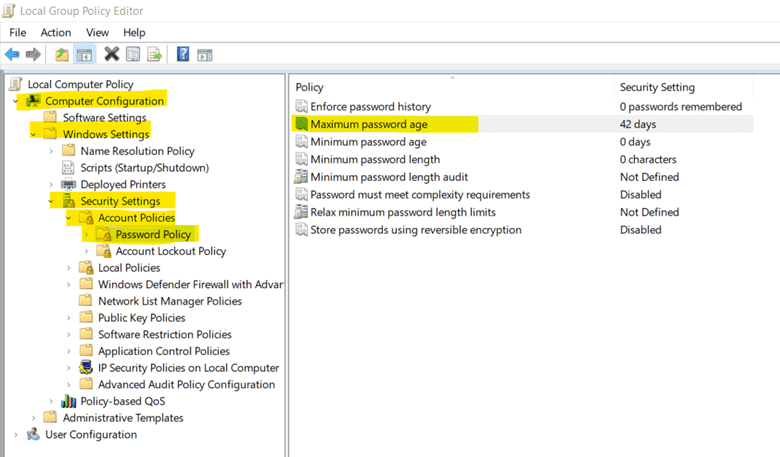
d. Click on Apply and OK.9. Set Maximum Password Age to Lower Limits
Password maximum age must be set to lower limits. So, the users will have to change their passwords frequently which will protect the user in case of a password breach or stolen password.
Steps to set this policy:
a. Open Group Policy Management Editor, you can do so by searching for Group Policy Management or by using "Windows + R" to open Run and write in it "gpedit.msc" and click "ok".
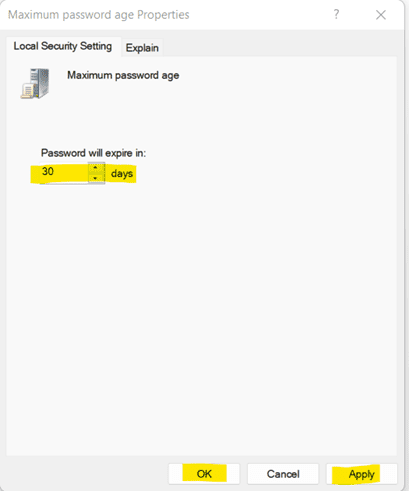
b. Under Computer Configuration, go to Windows Settings -> Security Settings -> Account Policies -> Password Policy. Then, open Maximum password age.c. Enter the numeric value (preferably 30 days).
d. Click on Apply and OK.
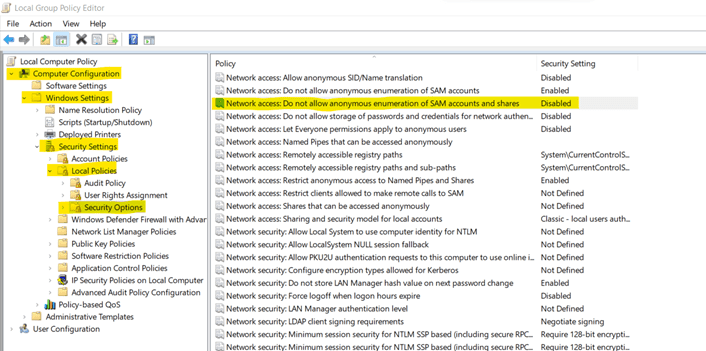
10. Disable Anonymous SID Enumeration
All security objects; Users, Groups, and others are assigned unique Security Identifier (SID) numbers. This is viable to be hacked by attackers and important data can be breached. By default, this policy setting is set to disabled, but ensure that this setting remains the same.
Steps to set this policy:
a. Open Group Policy Management Editor, you can do so by searching for Group Policy Management or by using "Windows + R" to open Run and write in it "gpedit.msc" and click "ok".
b. Under Computer Configuration, go to Windows Settings -> Security Settings -> Local Policies -> Security options. Then, open Network Access: Do not allow anonymous enumeration of SAM accounts and shares.
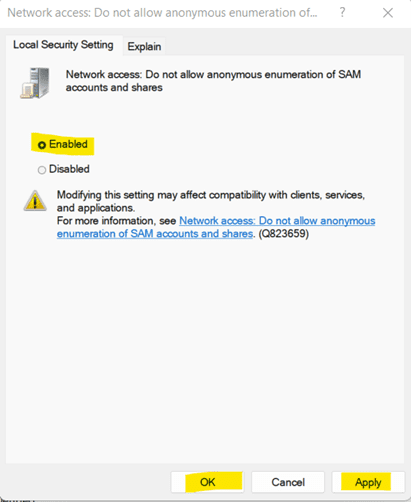
c. Select Enabled from the given options.
d. Click on Apply and OK.
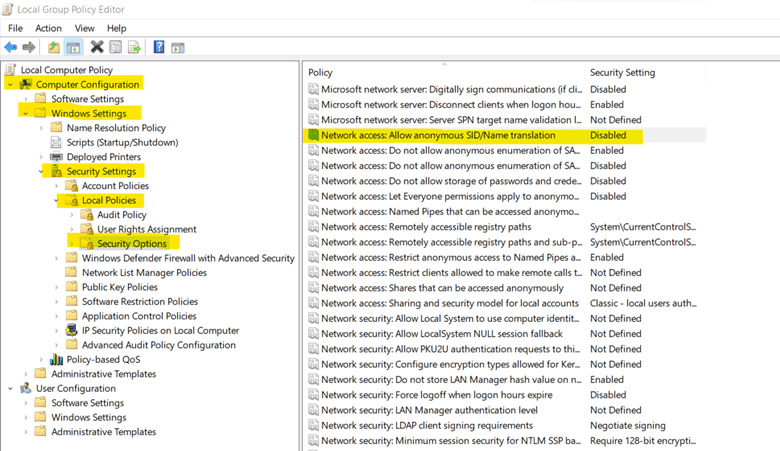
11. Disable SID/Name Translation
This Group Policy Setting determines whether an anonymous user can get access to the system or not by asking for Security Identifiers (SID). If Enabled, this setting will allow a user to anonymously submit SID of Administrator account making it prone to data breach. The preferred state for this group policy setting is "Disabled".
Steps to set this policy:
a. Open Group Policy Management Editor, you can do so by searching for Group Policy Management or by using "Windows + R" to open Run and write in it "gpedit.msc" and click "ok".
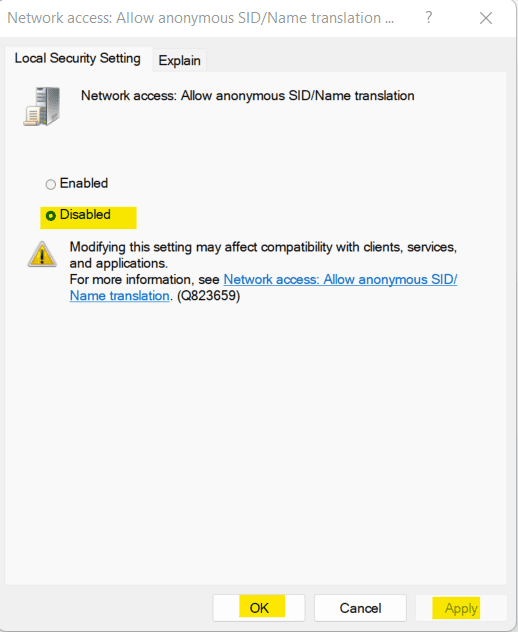
b. Under Computer Configuration, go to Windows Settings -> Security Settings -> Local Policies -> Security options. Then, open Network Access: Allow anonymous SIS/Name translation.
c. Select Disabled from the given options.
d. Click on Apply and OK.
GPO Best Practices
An attacker who successfully exploited the GPO vulnerability could run processes in an elevated context. Not having a system that automatically monitors vulnerabilities can provide an attacker with full access and control over a compromised device.
It is important to follow the best practices for Group Policy Settings to prevent breaches and reduce the attack surface. Ensuring security standards and policies remain in effect require IT teams to repeat the hardening process on a regular basis and manually monitor their operations if they do not have an automated remediation process in place.
Why automated baseline hardening?
Managing a huge IT infrastructure and ensuring security, productivity, and a uniform user experience is a challenge for organizations. A bit of fine tuning to your Group Policy settings can help regulate a user’s work environment, and seamlessly manage your operating systems and applications.
- If you want to remain in full control of your IT infrastructure, you have to make sure no unwanted changes in these policies and other Group Policies are made. Manual auditing is time consuming and difficult to keep a continuous track of changes made.CalCom's Automate Hardening Suite (CHS) allows you to audit every change made to Group Policies in real time and rollback any unwanted or unplanned Group Policy change quickly. CHS eliminates outages and reduces hardening costs by indicating the impact of a security hardening change on the production services; and ensures a resilient, constantly hardened and monitored operations environment.