LAN Manager Authentication Level Explained
LAN Manager (LM) authentication level is a security setting that determines how Windows systems authenticate network connections. It is a legacy authentication protocol developed by Microsoft for use in older versions of Windows network operations. These operations include:
- Joining a domain
- Authenticating between Active Directory forests
- Authenticating to older Windows domains (pre-2000)
- Authenticating to non-Windows machines (since Windows 2000)
- Authenticating to non-domain machines
LAN Manager Authentication Protocols
There are three main protocols involved in LAN Manager Authentication:
- LM (Lan Manager): This is the oldest and least secure protocol. It transmits passwords in a weakly hashed format, making them vulnerable to brute-force attacks.
- NTLM (NT LAN Manager): An improvement over LM, NTLM uses a stronger hashing algorithm for passwords. However, it still has security weaknesses and is susceptible to man-in-the-middle attacks.
- NTLMv2 (NT LAN Manager v2): The most secure protocol of the three, NTLMv2 offers better protection against various attacks compared to LM and NTLM.
The LAN Manager Authentication Level setting allows you to choose which protocols your system will use or accept for authentication.
LAN Manager Policy Description
LAN Manager (LM) is a family of early Microsoft client/server software products that allows users to link personal computers together on a single network. Network capabilities include transparent file and printer sharing, user security features, and network administration tools. In Active Directory domains, the Kerberos protocol is the default authentication protocol. However, if the Kerberos protocol is not negotiated for some reason, Active Directory will use LM, NTLM, or NTLMv2.
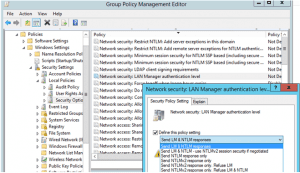
Network Security: LAN Manager Authentication Level Settings
The possible values for the Network security: LAN Manager authentication-level setting are:
- Send LM & NTLM responses –Clients use LM and NTLM authentication and never use NTLMv2 session security. Domain controllers accept LM, NTLM, and NTLMv2 authentication.
- Send LM & NTLM – use NTLMv2 session security if negotiated – Clients use LM and NTLM authentication and use NTLMv2 session security if the server supports it. Domain controllers accept LM, NTLM, and NTLMv2 authentication.
- Send NTLM responses only –Clients use NTLM authentication only and use NTLMv2 session security if the server supports it. Domain controllers accept LM, NTLM, and NTLMv2 authentication.
- Send NTLMv2 responses only –Clients use NTLMv2 authentication only and use NTLMv2 session security if the server supports it. Domain controllers accept LM, NTLM, and NTLMv2 authentication.
- Send NTLMv2 responses only\refuse LM –Clients use NTLMv2 authentication only and use NTLMv2 session security if the server supports it. Domain controllers refuse LM (accept only NTLM and NTLMv2 authentication).
- Send NTLMv2 responses only\refuse LM & NTLM –Clients use NTLMv2 authentication only and use NTLMv2 session security if the server supports it. Domain controllers refuse LM and NTLM (accept only NTLMv2 authentication).
- Not Defined
Potential Vulnerability
Default configurations per operating system:
*Windows Vista – Not Defined
*Windows 95-based and Windows 98-based clients only send LM.
*Windows 2000, Windows Server 2003, and Windows XP- send LM and NTLM authentication responses.
*Windows 95, Windows 98, and Windows NT operating systems cannot use the Kerberos version 5 protocol for authentication. For this reason, in a Windows Server 2003 domain, computers authenticate by default using both the LM and NTLM protocols.
By default, these servers let any client connect and access their resources. But this setup comes with a risk: it sends LM responses, which are the least secure way to authenticate. Attackers could intercept this traffic and quickly figure out the user’s password.
You can enforce a more secure authentication protocol for Windows 95, Windows 98, and Windows NT by using NTLMv2. For the logon process, NTLMv2 uses a secure channel to protect the authentication process. Even if you use NTLMv2 for earlier clients and servers, Windows-based clients and servers that are members of the domain will use the Kerberos authentication protocol to authenticate with Windows Server 2003 domain controllers.
Countermeasures
Configure the Network security: LAN Manager Authentication Level setting to Send NTLMv2 responses only. We recommend this level of authentication when all clients support NTLMv2.
Potential Impact
Clients that do not support NTLMv2 authentication will not be able to authenticate in the domain and access domain resources by using LM and NTLM.
Severity of Setting
Critical
How to Configure
To configure NTLM compatibility for Windows Vista and Windows 7:
- Click Start > All Programs > Accessories > Run and type secpol.msc in the Open box, and then click OK.
- Click Local Policies > Security Options > Network Security: LAN Manager authentication level.
- Click Send LM & NTLM – use NTLMv2 session security if negotiated.
- Click Apply.
Configuring GPO to Force NTLMv2
Go to the GPO section Computer Configurations -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Security Options and find the policy Network Security: LAN Manager authentication level.
You can also disable NTLMv1 through the registry. To do it, create a DWORD parameter with the name LmCompatibilityLevel and the value 0-5 in the registry key HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Lsa. Value 5 corresponds to the policy option "Send NTLMv2 response only. Refuse LM NTLM".