Password Policies
A password policy is a set of rules that are usually a part of an organizations security regulations to improve computer security. These policies can be formal regulations or part of security awareness training programs that outline requirements such as minimum length, complexity and unique characters.
A password must comply with these password strength rules to be set for an account. These options specify the standards and rules for a password:
- Minimum and Maximum Password Age
- Enforced Password History
- Minimum Password Length
- Password meeting Complexity Requirements
- Storing Passwords using Reversible Encryption
What is an example of a password policy?
Below are a few of the examples security frameworks request businesses to comply with regarding their password policy:
CIS Password Policy Recommends:
‘Maximum password age’ is set to ’60 or fewer days, but not 0′ TO ‘365 or fewer days, but not 0’
CISA Password Policy Recommends:
- Long-at least 16 characters long (even longer is better).
- Random-like a string of mixed-case letters, numbers and symbols (the strongest!) or a passphrase of 5 -7 random words.
- Unique-used for one and only one account.
NIST Password Policy Recommends:
- Verifier should not impose composition rules e.g., requiring mixtures of different character types or prohibiting consecutively repeated characters
- Verifier should not require passwords to be changed arbitrarily or regularly e.g. the previous 90 day rule
- Passwords must be at least 8 characters in length
- Password systems should permit subscriber-chosen passwords at least 64 characters in length.
Default Password Policy
When a domain controller (DC) is configured it comes with a pre-defined set of rules and standards to make sure a password is secure. These are:
You can view your default password policy by following the steps mentioned below:
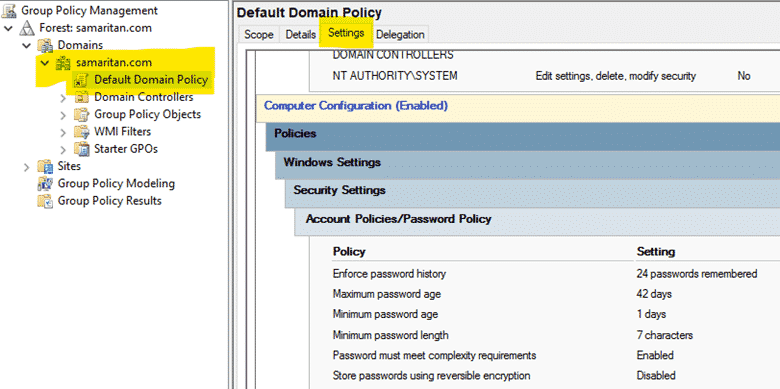
- Open your "Windows Server Manager". Go to "Tools" and then to "Group Policy Management".
2. In "Group Policy Management", expand your "Forest" -> "Domains" -> "yourdomain.com". Then click on "Default Domain Policy" -> "Settings". Scroll down and in the "Policies" section under "Account Policies/Password Policy", you can see your Password Policy Settings.
Custom Password Policy
Default password policy comes with fundamental level security, but if your company needs a more secure password you have the option of editing the "Default Domain Policy" this can be done by following the steps below:
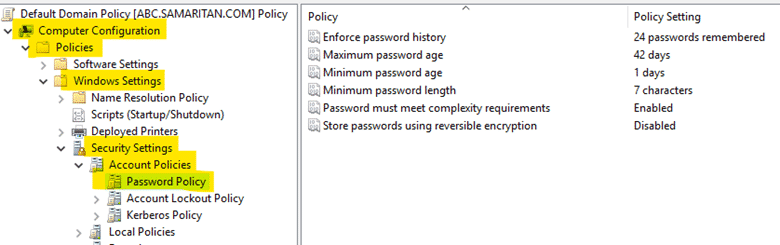
- Go to "Tools" -> "Group Policy Management", expand "Forest" -> "Domains" -> "yourdomain.com", right-click on "Default Domain Policy" and select "Edit".
2. In "Group Policy Management Editor", under "Computer Configuration", expand "Policies" -> "Windows Settings" -> "Security Settings" -> "Account Policies", then click on "Password Policy".
3. Here, you can change the settings for all of the policies according to your organizational requirement.
What is the standard password policy
Certain settings are recommended by Microsoft's Security Compliance Toolkit which will improve the security of Active Directory. These recommended settings are:
| Policy | Policy Setting |
| Enforce Password History | 24 |
| Maximum Password Age | 60 or fewer |
| Minimum Password Age | 1 or more |
| Minimum Password Length | 14 |
| Password must meet Complexity Requirements | Enabled |
| Store Passwords Using Reversible Encryption | Disabled |
Is Not Defined the same as Disabled?
The answer to this question is NO. The term “Not Defined" and "Disabled" have their differences. Even if we go to the literal meanings of these terms we'll find out that both these terms are different from each other. However, we can briefly explain these terms by implementing them on our Active Directory.
Now, let us take an example of the policy "Store passwords using reversible encryption". This concept is explained in the steps mentioned below:
- Set "Store passwords using reversible encryption" -> Enabled, the system will store passwords using reversible encryption.
- Set "Store passwords using reversible encryption" -> Not Defined, the system will store passwords using reversible encryption.
- Set "Store passwords using reversible encryption" -> Disabled, the system will not store passwords using reversible encryption.
- Set "Store passwords using reversible encryption" -> Not Defined, the system will not store passwords using reversible encryption.
So, summarizing it, we can see that when the status for the "Store passwords using reversible encryption" policy was changed from "Enabled" to "Not Defined", it kept the last status of "Enable". Similarly, when we changed the status of the "Store passwords using reversible encryption" policy from "Disabled" to "Not Defined", it kept the last status of "Disable".
Password Attacks
Attackers use a number of techniques to compromise passwords, some of these techniques are:
- Brute force Attack. In this technique a hacker runs a program that inserts various password combinations and if you have a weak password then you are at risk of falling prey to this attack.
- Dictionary Attack. This is a special type of brute force attack in which words from a dictionary are used as possible keywords.
- Credential Studding Attack. Attackers use various automated tools that enters a list of credentials against several company login portals.
- A malicious user collects data of a possible target and then tries to generate password combinations using the collected data.
Securing enterprise assets & software
CIS Control 4: Secure Configuration of Enterprise Assets and Software discusses the default configurations of assets and software. Generally, these configurations are set for easy deployment and use rather than security which means having default passwords enabled.
These security configuration updates need to be managed and maintained with configuration updates tracked and approved through a configuration management workflow to maintain records that can be reviewed for compliance and to support audits. CalCom Hardening Suite (CHS) automates this labor-intensive task of security-policy testing and learns the current security configuration and status of each server then states the impact of any policy change on production environments. Using CHS, the policy implementation process becomes a one-time effort which automatically re-hardens servers following any unauthorized change - in real-time - ensuring continuous compliance with security policies.