January 2020 is when the Department of Defense (DoD) released the Cyber Maturity Model Certification (CMMC) framework, aimed at evaluating and strengthening the cybersecurity readiness of the Defense Industrial Base (DIB). As per the DoD’s directive, all prime contractors and subcontractors within the supply chain must undergo auditing and certification under the CMMC framework. This necessitates specific adaptations by the companies within the supply chain, yet serves to fortify the DoD against potential cyber threats, thereby mitigating future losses resulting from breaches.
The National Institute of Standards and Technology (NIST) created the NIST Special Publication 800-171 (NIST 800-171). NIST is a non-regulatory agency of the United States Department of Commerce that develops and issues guidelines, standards, and best practices to enhance the security and resilience of information systems and infrastructure across various sectors. NIST 800-171 specifically focuses on safeguarding Controlled Unclassified Information (CUI) in non-federal systems and organizations.
CMMC Model Structure
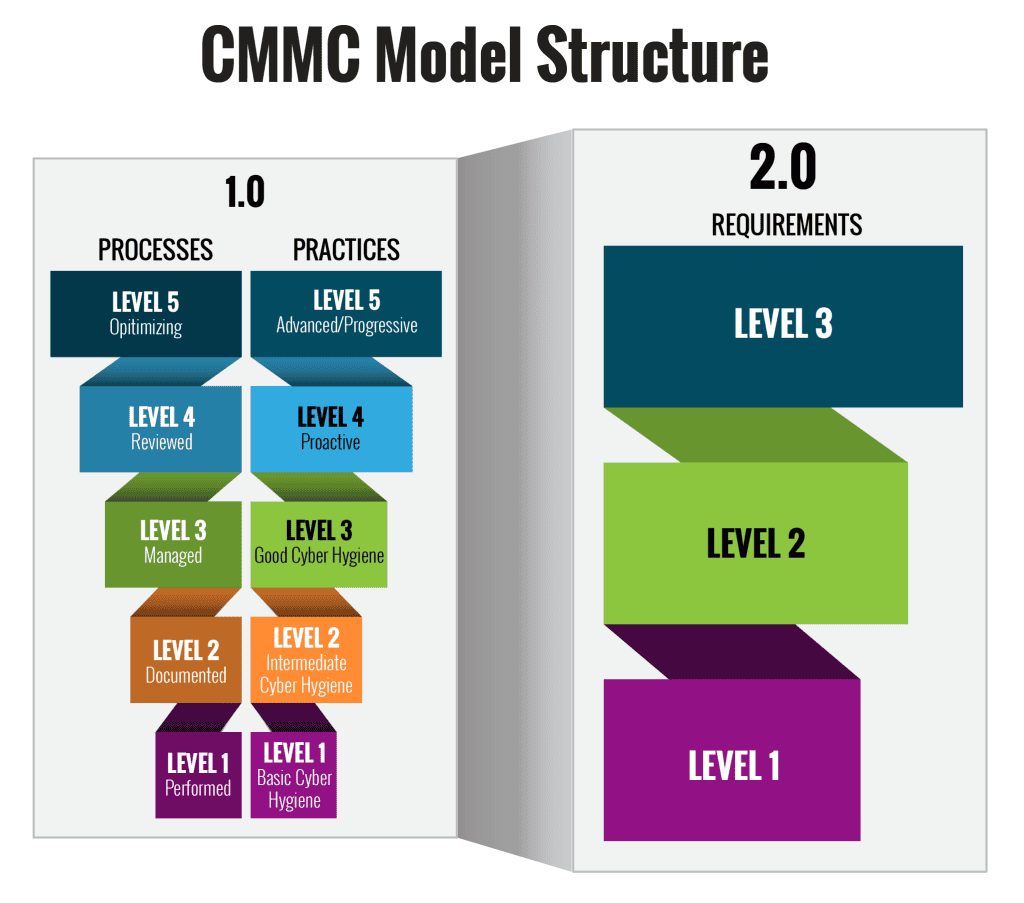
CMMC underwent a significant change from its original version of 5 levels to 3 levels in November 2021. CMMC 2.0 is a revised program framework and criteria aimed at fulfilling the core objectives of the internal review:
- Safeguarding sensitive information to empower and safeguard the warfighter.
- Enforcing cybersecurity standards within the Defense Industrial Base (DIB) to address evolving threats.
- Ensuring accountability while reducing obstacles to compliance with Department of Defense (DoD) regulations.
- Fostering a cooperative environment of cybersecurity and cyber resilience.
- Upholding public trust through adherence to high professional and ethical standards.
The major adjustments to the original CMMC Model include:
- Revising the Levels, reducing Level 5 to Level 3. Level 1 remained unchanged, while the new Level 2 aligned with the former Level 3, and the new Level 3 mirrored the previous Level 5.
- Eliminating the prohibition on Plans of Action and Milestones (POAMs) for Level 1 and certain Level 2 requirements.
- Transforming Level 1 into a self-attestation process for contractor organizations, replacing the initial mandate of third-party assessment by designated assessment entities.
- Adapting the less critical controls in Level 2 to also be self-attested by contractor organizations.
CMMC vs NIST 800-171
The primary distinction between CMMC vs NIST 800-171 lies in their respective roles: NIST 800-171 serves is a set of guidelines established by the National Institute of Standards and Technology (NIST) to help businesses protect their systems and data, whereas CMMC (Cybersecurity Maturity Model Certification) is a certification program developed by the DoD that improves cybersecurity for contractors and outlines the pathway to achieving compliance with NIST.
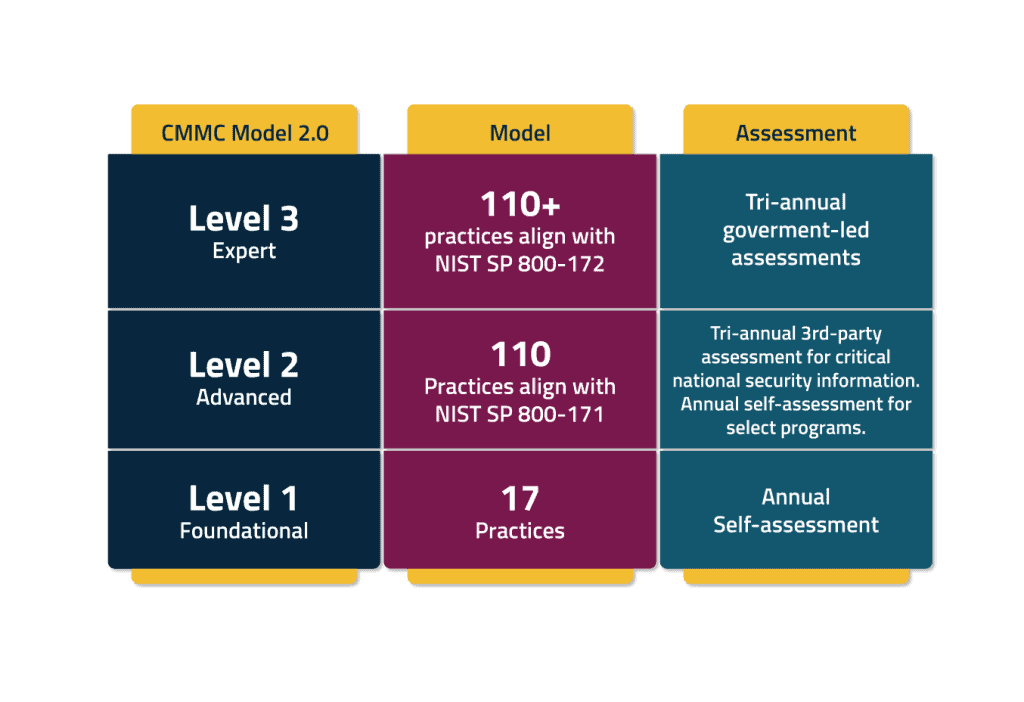
3 CMMC Levels
Level 1:
Foundational Cyber Hygiene Standard: At this level, organizations must establish fundamental cybersecurity measures commonly adopted by businesses. To attain Level 1 status, companies are required to enforce 17 controls outlined in NIST SP 800-171 Rev2.
Level 2:
Advanced Cyber Hygiene Standard: This level necessitates the implementation of all 110 controls specified in NIST SP 800-171 Rev2 to attain certification at Level 2.
Level 3:
Expert Practice: At this stage, companies must demonstrate the execution, evaluation, and maintenance of advanced cybersecurity procedures across their operations. In addition to implementing all controls from NIST 800-171, organizations are required to incorporate an additional subset of controls from NIST 800-172.
Which level of CMMC is most closely aligned with NIST 800-171?
CMMC Level 2 closely aligns with NIST 800-171 because it incorporates its foundational security requirements while adding further measures to enhance cybersecurity maturity, making it a logical progression for organizations seeking to meet both standards.
CMMC Level 2 also builds upon the foundational security requirements outlined in NIST 800-171. NIST 800-171 provides a set of security controls and guidelines aimed at protecting Controlled Unclassified Information (CUI) in non-federal systems and organizations. CMMC Level 2, on the other hand, requires implementing practices from NIST 800-171 and adds additional security measures to enhance cybersecurity maturity.
Summit 7 provides a very informative video about NIST SP 800-171 Updates:
CMMC Level 2 encompasses practices that directly correspond to the security controls specified in NIST 800-171. These practices include measures related to access control, awareness and training, incident response, configuration management, and other aspects of cybersecurity outlined in NIST 800-171. Therefore, achieving compliance with CMMC Level 2 essentially means adhering to the requirements of NIST 800-171 while also demonstrating a certain level of maturity in implementing these controls.
DFARS & NIST 800-171
DFARS along with NIST 800-171 are essential compliance standards for most government contracts. To meet DFARS requirements, it’s necessary to adhere to all 110 controls outlined in NIST 800-171. While DFARS doesn’t cover CMMC, a new clause is in progress specifically for this purpose.
CMMC Implementation Timeline
The Department of Defense (DoD) is still working on when exactly they’ll start using CMMC 2.0 in their contracts, but they’ve given some guidance. It’s expected to start appearing in contracts by the end of 2024 or early 2025. The DoD has already begun including CMMC requirements in some contract evaluations, like requests for information (RFIs) and proposals (RFPs). This means that meeting CMMC standards is now part of what the DoD looks at when deciding who gets certain contracts.
Contractors who do not meet applicable CMMC requirements could miss out on the opportunity to compete for new contracts or could have their existing DoD contracts end after option periods are not exercised.
In terms of CMMC compliance, CalCom Hardening Suite (CHS) primary function is to decrease operational expenses while mitigating the risk of production interruptions by directly showcasing the impact of security baseline adjustments on the production environment. CHS eliminates the necessity of testing changes in a lab environment prior to their implementation in production.
Key Advantages:
- Implement security policies seamlessly without disrupting the production environment.
- Decrease expenses and resource allocation necessary for secure configuration implementation and compliance posture.
- Oversee the entire infrastructure hardening process through a centralized control point.
- Prevent configuration drifts and the need for recurrent hardening procedures.
If you're interested in learning how to be more competitive and not miss out on a DoD contact, Get in Touch.