With the rise of cyber threats and the increasing volume of sensitive data being transmitted over networks, organizations must prioritize the use of cryptographic algorithms that meet stringent standards for security and reliability. One such standard is FIPS (Federal Information Processing Standards) compliance, which ensures that cryptographic algorithms adhere to the rigorous criteria set forth by the U.S. government. In this blog post, we delve into the significance of FIPS compliant cryptography and its role in safeguarding data integrity and confidentiality.
What it means to be FIPS compliant
FIPS compliance is a certification awarded to cryptographic algorithms and modules that meet the standards outlined by the National Institute of Standards and Technology (NIST) in the United States. These standards are designed to ensure the security and interoperability of cryptographic implementations across various systems and applications. FIPS compliant algorithms undergo rigorous testing and validation processes to demonstrate their effectiveness in protecting sensitive information against unauthorized access and manipulation.
Encryption: Shielding Data from Prying Eyes
Encryption lies at the heart of modern cybersecurity, serving as a crucial tool for protecting data both at rest and in transit. FIPS compliant encryption algorithms, such as the Advanced Encryption Standard (AES), employ robust mathematical techniques to scramble plaintext data into ciphertext, rendering it unreadable to anyone without the corresponding decryption key. By adhering to FIPS standards, organizations can trust that their encryption mechanisms provide a high level of security against brute-force attacks and other cryptographic vulnerabilities.
Hashing: Verifying Data Integrity
Hash functions play a vital role in ensuring the integrity of data by generating unique fixed-size hash values for arbitrary input. FIPS compliant hashing algorithms, such as SHA-256 (Secure Hash Algorithm 256-bit), produce hash values that are resistant to collision attacks and tampering attempts. These algorithms are widely used for tasks such as password hashing, digital signatures, and data integrity verification, providing a reliable means of confirming the authenticity and integrity of digital information.
Signing: Authenticating Identities and Messages
Digital signatures serve as digital fingerprints, providing a means of authenticating the origin and integrity of electronic documents and messages. FIPS compliant signature algorithms, such as RSA (Rivest-Shamir-Adleman) and ECDSA (Elliptic Curve Digital Signature Algorithm), use cryptographic techniques to create unique signatures that can be verified by anyone with access to the corresponding public key. By adhering to FIPS standards for signature generation and verification, organizations can establish trust in the authenticity of digital communications and transactions.
Implementing FIPS Compliant Cryptography
Achieving FIPS compliance requires careful selection and implementation of cryptographic algorithms and modules that have undergone rigorous testing and validation processes. Organizations can leverage cryptographic libraries and modules, such as OpenSSL and Microsoft CNG (Cryptography API: Next Generation), that offer FIPS compliant functionality out of the box. Additionally, it’s essential to stay informed about the latest FIPS guidelines and updates to ensure ongoing compliance with evolving security standards and regulations.
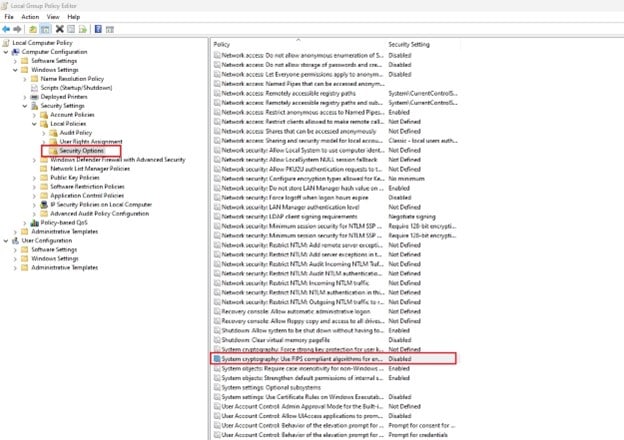
Steps to follow to enable this setting.
- Open start menu and search for "Group Policy Editor".
- Navigate to the following path Computer Configuration\Windows Settings\Security Settings\Local Policies\Security
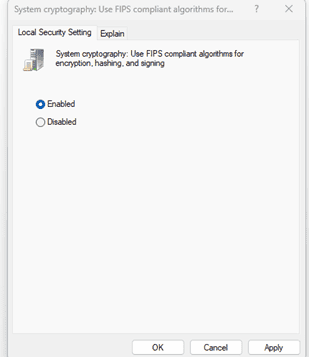
- Open the setting named as System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing
- Enable the setting and Click OK.
Enabling this setting does the following:
TLS/SSL
For the Schannel Security Service Provider (SSP), this security setting disables the weaker Secure Sockets Layer (SSL) protocols and supports only the Transport Layer Security (TLS) protocols as a client and as a server (if applicable). If this setting is enabled, Transport Layer Security/Secure Sockets Layer (TLS/SSL) Security Provider uses only the FIPS 140 approved cryptographic algorithms: 3DES and AES for encryption, RSA or ECC public key cryptography for the TLS key exchange and authentication, and only the Secure Hashing Algorithm (SHA1, SHA256, SHA384, and SHA512) for the TLS hashing requirements.
Encrypting File System Service (EFS)
For Encrypting File System Service (EFS), it supports the Triple Data Encryption Standard (DES) and Advanced Encryption Standard (AES) encryption algorithms for encrypting file data supported by the NTFS file system. By default, EFS uses the Advanced Encryption Standard (AES) algorithm with a 256-bit key in the Windows Server 2003 and Windows Vista family and DESX algorithm in Windows XP for encrypting file data. For information about EFS, see Encrypting File System.
Remote Desktop Services
For Remote Desktop Services, it supports only the Triple DES encryption algorithm for encrypting Remote Desktop Services network communication.
Note: Remote Desktop Services was called Terminal Services in previous versions of Windows Server.
BitLocker
For BitLocker, this policy needs to be enabled before any encryption key is generated. Recovery passwords created when this policy is enabled are incompatible with BitLocker on Windows 8, Windows Server 2012, and earlier operating systems. If this policy is applied to computers running operating systems prior to Windows 8.1 and Windows Server 2012 R2, BitLocker will prevent the creation or use of recovery passwords; recovery keys should be used for those computers instead.
How does OpenShift achieve FIPS compliance?
OpenShift's cryptographic components are FIPS compliant. When Red Hat OpenShift 4 is deployed on FIPS-enabled Red Hat Enterprise Linux CoreOS (RHCOS) nodes or Red Hat Enterprise Linux (RHEL) worker nodes, correctly compiled OpenShift platform Golang binaries will use RHEL FIPS validated or Modules in Process OpenSSL instead of the standard Golang cryptographic module.
Some components include OpenSSL directly in their builds and use it for cryptography regardless of whether the cluster is booted in FIPS mode, with one such component being HAProxy.
Support for FIPS cryptography
You can install an OpenShift Container Platform cluster that uses FIPS validated or Modules in Process cryptographic libraries on the x86_64 architecture.
For the Red Hat Enterprise Linux CoreOS (RHCOS) machines in your cluster, this change is applied when the machines are deployed based on the status of an option in the install-config.yaml file, which governs the cluster options that a user can change during cluster deployment. With Red Hat Enterprise Linux (RHEL) machines, you must enable FIPS mode when you install the operating system on the machines that you plan to use as worker machines. These configuration methods ensure that your cluster meets the requirements of a FIPS compliance audit: only FIPS validated or Modules In Process cryptography packages are enabled before the initial system boot.
Because FIPS must be enabled before the operating system that your cluster uses boots for the first time, you cannot enable FIPS after you deploy a cluster.
To enable the cryptographic module self-checks mandated by the Federal Information Processing Standard (FIPS) 140, enable FIPS mode during the system installation. Only enabling FIPS mode during the RHEL installation ensures that the system generates all keys with FIPS-approved algorithms and continuous monitoring tests in place.
Procedure
- Add the fips=1 option to the kernel command line during the system installation.
- During the software selection stage, do not install any third-party software.
- After the installation, the system starts in FIPS mode automatically.
Verification
After the system starts, check that FIPS mode is enabled:
fips-mode-setup -check
FIPS Compliance
Ensuring compliance with FIPS (Federal Information Processing Standards) in cryptographic implementations can be a daunting task fraught with challenges. Integrating FIPS compliant algorithms into existing systems often proves complex, requiring meticulous configuration and compatibility checks across diverse platforms. Moreover, the stringent security requirements of FIPS-compliant algorithms may introduce performance overheads, impacting system responsiveness and efficiency, particularly when handling large volumes of data or intensive cryptographic operations. Maintenance and updates further compound the challenge, as organizations must navigate the complexities of managing patches and ensuring ongoing compliance with evolving standards and regulations.
By providing pre-configured templates, automated workflows, and performance optimization features, an automated hardening tool streamlines security benchmarks, enabling organizations to uphold the security and integrity of their systems with ease and confidence.