What is a cipher suite?
Cipher suites are a set of cryptographic algorithms utilized by the schannel SSP implementation of TLS/SSL protocols. These algorithms are employed to generate keys and encrypt data. Each cipher suite designates specific algorithms for the following functions:
- Key exchange
- Bulk encryption
- Message authentication
Obsolete cipher suites
In TLS 1.2 and TLS 1.3, the NSA suggests using cryptographic settings that meet the standards in CNSSP 15, known as Commercial National Security Algorithms.
In TLS 1.2, “cipher suites” are the agreed-upon combinations of cryptographic methods for secure communication. The client offers a list of cipher suites, and the server selects one from that list. Each suite includes an encryption method, authentication mechanism, key exchange method, and key derivation mechanism.
Weak cipher suites are outdated cipher suites making them weak. Weak encryption methods in TLS 1.2 include NULL, RC2, RC4, DES, IDEA, and TDES/3DES, and should be avoided. TLS 1.3 removes these outdated suites, but systems supporting both versions should still be checked for them.
Configure SSL cipher list via GPO
The SSL cipher list is configured to limit the available cipher suites before establishing an encrypted SSL connection. This list consists of one or more cipher suite strings separated by colons. It’s important to note that all cipher strings are case insensitive.
The default value for this configuration is:
“ECDHE-RSA-AES256-GCM-SHA384:AES256-SHA256:AES256-SHA:ECDHE-RSA-AES128-GCM-SHA256:AES128-SHA256:AES128-SHA:@STRENGTH”
If this configuration is applied, the checkbox labeled “Enforce AES-256 or stronger ciphers for SSL connection negotiation” in “Configure SSL connections to satisfy Security Tools” will be disregarded.
It’s essential to apply this setting to both the PCoIP server and PCoIP client simultaneously.
Configure SSL cipher list
| Registry Hive | HKEY_LOCAL_MACHINE |
| Registry Path | Software\Policies\Teradici\PCoIP\pcoip_admin_defaults |
| Value Name | pcoip.ssl_cipher_list |
| Value Type | REG_SZ |
| Default Value | ECDHE-RSA-AES256-GCM-SHA384:AES256-SHA256:AES256-SHA:ECDHE-RSA-AES128-GCM-SHA256:AES128-SHA256:AES128-SHA:@STRENGTH |
TLS/SSL weak message authentication code cipher suites
It is recommended to order SSL ciphers by strength when receiving TLS/SSL weak message authentication code cipher suites. Ordering SSL ciphers by strength may cause the virtual server to process fewer SSL transactions per second (TPS).
If you enable 'SSL Cipher Suite Order' policy setting via the GPO, SSL cipher suites are prioritized in the order specified. If you disable or do not configure this policy setting, default cipher suite order is used.
SSL Cipher Suites
| Registry Hive | HKEY_LOCAL_MACHINE |
| Registry Path | SOFTWARE\Policies\Microsoft\Cryptography\Configuration\SSL\00010002 |
| Value Name | Functions |
| Value Type | REG_SZ |
| Default Value | TLS_AES_256_GCM_SHA384,TLS_AES_128_GCM_SHA256,TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_DHE_RSA_WITH_AES_256_GCM_SHA384,TLS_DHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,TLS_RSA_WITH_AES_256_GCM_SHA384,TLS_RSA_WITH_AES_128_GCM_SHA256,TLS_RSA_WITH_AES_256_CBC_SHA256,TLS_RSA_WITH_AES_128_CBC_SHA256,TLS_RSA_WITH_AES_256_CBC_SHA,TLS_RSA_WITH_AES_128_CBC_SHA,TLS_RSA_WITH_3DES_EDE_CBC_SHA,TLS_RSA_WITH_NULL_SHA256,TLS_RSA_WITH_NULL_SHA,TLS_PSK_WITH_AES_256_GCM_SHA384,TLS_PSK_WITH_AES_128_GCM_SHA256,TLS_PSK_WITH_AES_256_CBC_SHA384,TLS_PSK_WITH_AES_128_CBC_SHA256,TLS_PSK_WITH_NULL_SHA384,TLS_PSK_WITH_NULL_SHA256 |
TLS 1.3 cipher suites
Suites typically use Transport Layer Security (TLS) or its deprecated predecessor Secure Socket Layer (SSL). There are hundreds of different cipher suits containing different combinations of algorithms such as key exchange algorithm, bulk encryption algorithm, Message Authenticaion Code (MAC) algorithm; however with TLS 1.3 only 5 cipher suites have been supported and defined.
TLS 1.3 supports these 5 cipher suites:
- TLS_AES_128_GCM_SHA256
- TLS_AES_256_GCM_SHA384
- TLS_CHACHA20_POLY1305_SHA256
- TLS_AES_128_CCM_SHA256
- TLS_AES_128_CCM_8_SHA256
TLS 1.3 introduces a shift in how machines coordinate cipher suites. The handshake process now determines the cipher suite for two communicating machines. TLS 1.3 has streamlined the handshake process to reduce the number of messages exchanged. This minimizes processing requirements, packet traffic, and enhances efficiency compared to earlier TLS versions.
Obsolete key exchange mechanisms
Cipher suites that use key exchange mechanisms that are designated as EXPORT or ANON are considered as obsolete and should not be used. In addition, specific configurations should be implemented on other key exchange methods. TLS key exchange methods include RSA key transport and DH or ECDH key establishment. DH and ECDH can either use static or ephemeral mechanisms.
Here are NSA key exchange mechanisms recommendations:
- RSA key transport and ephemeral DH or ECDH should couple with RSA or ephemeral using at least 3072-bit keys.
- Key exchanges with ephemeral ECDH key only when using secp384r1 elliptic curve.
- For RSA key transport and DH or DHE key exchange, you should not use keys that are less than 2048 bits.
- Ephemeral CDH or ECDH using custom curves should not be used.
The NSA recommends replacing obsolete protocol configurations with ones that provide better encryption and authentication.
Detecting obsolete configurations
NSA's recommended detection strategy contains three stages:
Stage 1: identify clients and servers which are using old TLS versions. If a client offers or a server accept any old TLS or SSL version, traffic should be blocked immediately.
Stage 2: when TLS 1.2 is in use, you should detect whether the traffic is based on an obsolete cipher suite.
Stage 3: when TLS 1.2 or TLS 1.3 are in use with the right cipher suites, key exchange mechanisms should be investigated. If a weak key exchange method is detected, it should be blocked.
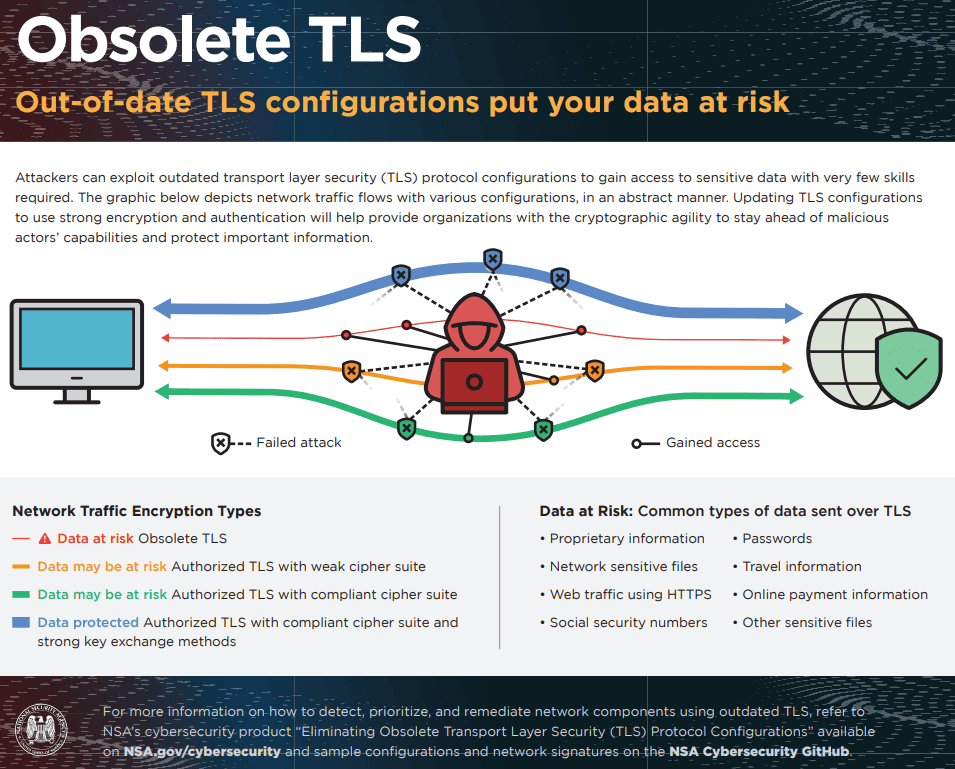
Vulnerabilities
The security of a cipher suite depends on the strength of the algorithms it includes. If the encryption or authentication algorithms within a cipher suite have known vulnerabilities, both the cipher suite and the TLS connection could become vulnerable. Consequently, a prevalent attack on TLS and cipher suites is referred to as a downgrade attack. This type of attack transpires when a modern client connects to outdated legacy servers using older versions of TLS or SSL.
Disable TLS/SSL support for static key cipher suites
Specify the TLS cipher suites to disable via the GPO. Set up the list of cipher suites to deactivate for TLS connections. When you set up this policy, the cipher suites listed won’t be used during TLS connections.
If you don’t set up this policy, the browser will select which TLS cipher suites to utilize.
Cipher suite values to be deactivated are specified as 16-bit hexadecimal values, assigned by the Internet Assigned Numbers Authority (IANA) registry.
The TLS 1.3 cipher suite TLS_AES_128_GCM_SHA256 (0x1301) is mandatory for TLS 1.3 and cannot be disabled through this policy.
This policy has no impact on QUIC-based connections. QUIC can be disabled via the ‘QuicAllowed’ (Allow QUIC protocol) policy.
Example value:
0x1303
0xcca8
0xcca9
Specify the TLS cipher suites to disable
| Registry Hive | HKEY_LOCAL_MACHINE or HKEY_CURRENT_USER |
| Registry Path | Software\Policies\Microsoft\Edge\TLSCipherSuiteDenyList |
| Value Name | {number} |
| Value Type | REG_SZ |
| Default Value |
TLS/SSL Cipher Hardening
Using strong encryption for network traffic in data transit is essential for information security. But using an updated TLS version is not enough. Organizations must take into consideration the cipher suites and key exchange methods that are being used both by the server and the client.
The default SSL/TLS configurations on many servers are not secure enough. Typically, these servers still maintain support for outdated and vulnerable protocol versions by default. Such configurations could render servers susceptible to attacks.
Automated configuration hardening is necessary, otherwise manual configurations need to be applied to each server. Automation provides scalability, increased security, improved auditability, and reduced risk of human error