System Cryptography Explained
In today’s digitally interconnected world, where data flows freely across networks and devices, ensuring its security is paramount. This is where system cryptography steps in, offering a suite of tools and techniques to safeguard sensitive information from prying eyes and malicious actors. Let’s delve deeper into the realm of system cryptography, exploring its intricacies and significance in modern computing.
System cryptography, at its core, revolves around the utilization of cryptographic algorithms and protocols within computer systems to ensure the confidentiality, integrity, and authenticity of data. This multifaceted discipline encompasses a myriad of cryptographic methodologies, ranging from classical symmetric and asymmetric encryption to cutting-edge quantum cryptographic paradigms.
Example of Cryptography system
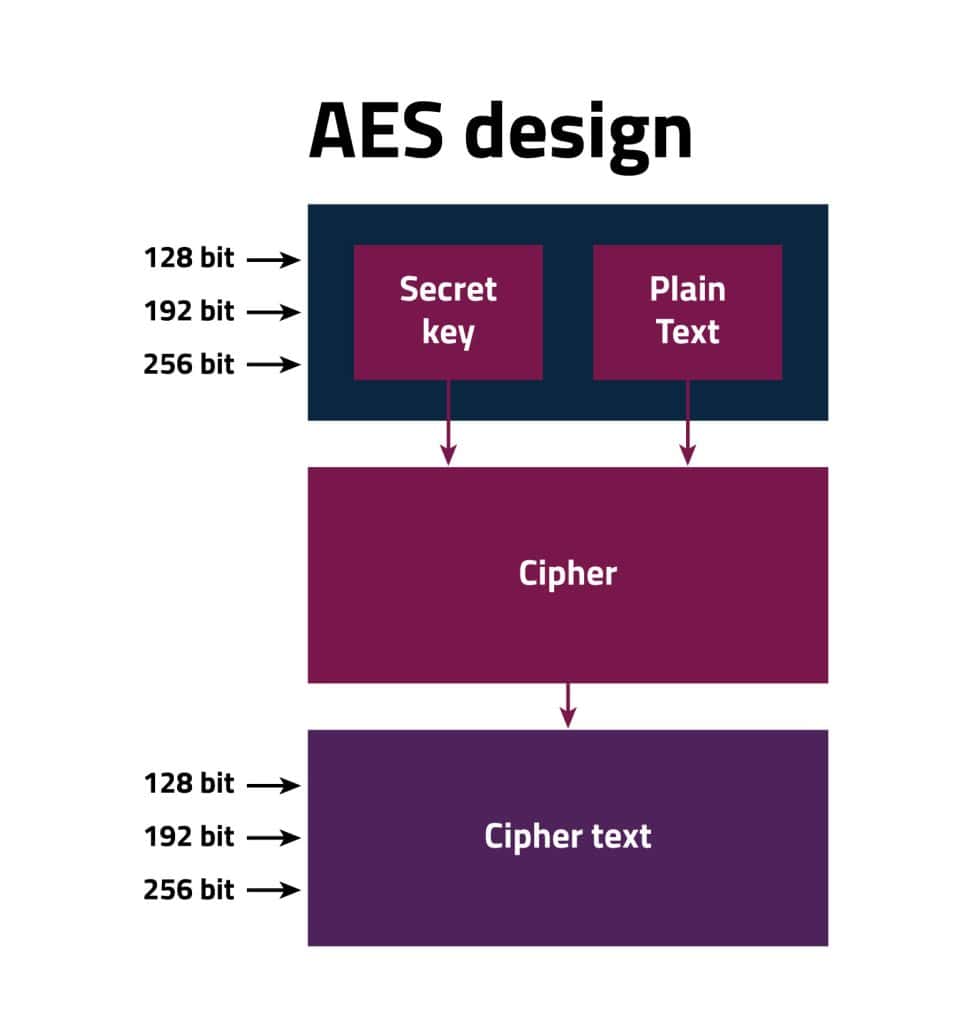
The Advanced Encryption Standard (AES) is a symmetric block cipher that the U.S. government has adopted to safeguard classified information. It’s extensively deployed globally, both in software and hardware, to encrypt sensitive data, playing a vital role in government computer security, cybersecurity, and electronic data protection. AES ensures security and reliability by subjecting data to multiple encryption rounds and segmenting messages into smaller blocks of 128 bits, making it more secure compared to older symmetric encryption techniques.
Being a symmetric encryption algorithm and a block cipher, AES utilizes the same key for both encryption and decryption processes, unlike asymmetric algorithms that use different keys for encryption and decryption. This requirement for a shared secret encryption key between the sender and receiver sets AES apart. Moreover, AES employs multiple cryptographic keys, each undergoing numerous encryption rounds, to enhance data protection, confidentiality, and integrity.
While AES-128 typically offers adequate security for most consumer applications, it may not suffice for highly sensitive information classified as Top Secret, such as government or military data. In such cases, stronger security measures provided by AES-192 or AES-256 are recommended, despite the potential requirement for more processing power and longer execution times.
In summary, AES is a critical component of modern cybersecurity infrastructure, providing robust encryption capabilities essential for protecting classified information across various sectors and applications.
Where is AES encryption used?
AES encryption is widely utilized across various sectors and applications due to its robust security features and versatility. Some prominent uses of AES encryption include:
- Data on storage media: AES encryption is commonly employed to secure data stored on hard drives, USB drives, and other storage devices, ensuring that sensitive information remains protected in case of theft or unauthorized access.
- Electronic communication apps: Many messaging and email platforms utilize AES encryption to safeguard the confidentiality of transmitted data, preventing interception or eavesdropping by malicious entities.
- Programming libraries: AES encryption is integrated into numerous programming libraries and frameworks, enabling developers to implement secure encryption features into their software applications.
- Internet browsers: Web browsers often employ AES encryption to establish secure connections (HTTPS) between users and websites, ensuring the confidentiality and integrity of data transmitted over the internet.
- File and disk compression: AES encryption can be used to encrypt compressed files or disk images, providing an additional layer of security for archived or compressed data.
- Wireless networks: AES encryption is a key component of Wi-Fi security protocols such as WPA2 and WPA3, safeguarding wireless communication between devices and access points from unauthorized access.
- Databases: AES encryption is commonly used to encrypt sensitive data stored in databases, protecting it from unauthorized access or data breaches.
- Login credentials including passwords: AES encryption is often employed to encrypt user passwords and authentication tokens stored in databases or transmitted over networks, ensuring that user credentials remain secure and confidential.
- Virtual private networking (VPN): AES encryption is integral to VPN protocols, such as IPSec and OpenVPN, providing secure and private communication over public networks by encrypting data traffic between VPN clients and servers.
Overall, AES encryption is a cornerstone of modern cryptography, widely adopted for its strong security guarantees and broad applicability across diverse encryption scenarios in both government and commercial settings.
How AES encryption works
AES encryption operates through a series of steps to transform plaintext into ciphertext, ensuring data confidentiality and integrity. Here’s a breakdown of how AES encryption works:
- Key Expansion: The AES algorithm begins by expanding the original encryption key into a set of round keys. Each round key is derived from the original key and is used in subsequent encryption rounds.
- Initial Round: In the first encryption round, the plaintext is XORed (exclusive OR) with the initial round key.
- Multiple Rounds: AES performs a series of encryption rounds, the number of which depends on the key length. For AES-128, there are 10 rounds; for AES-192, 12 rounds; and for AES-256, 14 rounds. Each round consists of several transformation steps:
- SubBytes: Each byte of the plaintext is substituted with a corresponding byte from a substitution table (S-box), which adds confusion to the data.
- ShiftRows: The rows of the state array (the current state of the data being encrypted) are shifted cyclically to create diffusion.
- MixColumns: The columns of the state array are mixed using a linear transformation to further spread the data throughout the block.
- AddRoundKey: The round key for the current round is XORed with the state array to introduce the key’s influence into the encryption process.
- Final Round: In the final encryption round, the SubBytes, ShiftRows, and MixColumns steps are performed as usual, but the MixColumns step is omitted. The AddRoundKey step XORs the state array with the final round key.
- Output: After the final round, the resulting state array represents the ciphertext, which is the encrypted form of the plaintext.
During decryption, the process is reversed:
- Key Expansion: The decryption key schedule is derived from the original encryption key.
- Initial Round: The ciphertext is XORed with the initial round key.
- Multiple Rounds: Similar to encryption, multiple rounds of decryption are performed, each consisting of the inverse transformations of SubBytes, ShiftRows, MixColumns, and AddRoundKey.
- Final Round: In the final decryption round, the MixColumns step is omitted, and the AddRoundKey step XORs the state array with the final round key.
- Output: The resulting state array represents the decrypted plaintext.
By performing these transformations and encryption rounds, AES ensures that even with knowledge of the algorithm and some ciphertext, it’s computationally infeasible to determine the original plaintext without knowledge of the encryption key. This provides strong security for encrypted data.
Advantages of AES
The AES algorithm provides several advantages over older algorithms such as the Data Encryption Standard (DES):
- AES offers stronger security since it incorporates multiple rounds of encryption, making it harder to break, and harder for threat actors to intercept or steal the encrypted information using brute-force attacks.
- AES is an open source and ubiquitously available solution, making it cost-effective to adopt and implement.
- AES is a flexible and simple algorithm, making it suitable for both hardware and software implementation.
4 Types of Cryptography
Cryptography can generally be categorized into four main types based on the operations they perform and the manner in which they operate:
Symmetric Key Cryptography:
Symmetric key cryptography, also known as secret-key cryptography, employs a single shared key for both encryption and decryption processes. The key is known only to the communicating parties, ensuring confidentiality. Symmetric algorithms are generally fast and efficient, making them suitable for encrypting large volumes of data. However, the primary challenge lies in securely distributing the secret key to all intended recipients. If the key is compromised, it compromises the security of all encrypted communications.
Common symmetric key algorithms include:
- Data Encryption Standard (DES): A widely used symmetric encryption algorithm, although it has largely been replaced by more secure algorithms like AES.
- Advanced Encryption Standard (AES): A successor to DES, AES is a widely adopted symmetric encryption standard known for its speed and security. It supports key lengths of 128, 192, or 256 bits.
Asymmetric Key Cryptography (Public Key Cryptography):
Asymmetric key cryptography utilizes a pair of keys: a public key for encryption and a corresponding private key for decryption. The public key is openly distributed, allowing anyone to encrypt messages intended for the owner of the corresponding private key. Conversely, the private key is kept secret and is used by the intended recipient to decrypt messages encrypted with the public key. Asymmetric cryptography resolves the key distribution problem inherent in symmetric cryptography. However, asymmetric algorithms are generally slower and require more computational resources than symmetric algorithms.
Common asymmetric key algorithms include:
- RSA (Rivest-Shamir-Adleman): Named after its inventors, RSA is widely used for secure communication, digital signatures, and key exchange.
- Diffie-Hellman Key Exchange: Used for secure key exchange between two parties over an insecure channel, without directly exchanging the encryption key.
Hash Functions:
Hash functions are mathematical algorithms that generate a fixed-size output (hash value or digest) from an input data of arbitrary size. These functions are one-way, meaning it is computationally infeasible to reverse the process and derive the original input from the hash. Hash functions ensure data integrity and authenticity by generating unique hash values for different inputs. Even a minor change in the input data results in a significantly different hash value. Hash functions are commonly used for data integrity verification, digital signatures, and password hashing.
Common hash functions include:
- SHA-256 (Secure Hash Algorithm 256-bit): Part of the SHA-2 family, SHA-256 generates a 256-bit hash value and is widely used for cryptographic applications.
- MD5 (Message Digest Algorithm 5): Although widely used in the past, MD5 is now considered cryptographically broken for most purposes due to vulnerabilities.
Steganography:
Steganography is the practice of concealing secret information within a carrier medium (such as images, audio files, or text) in such a way that it remains undetected by unintended recipients. Unlike encryption, which disguises the content of a message, steganography hides the existence of the message itself. Various techniques, such as embedding data in the least significant bits of digital files or using invisible ink, are employed for steganographic purposes. Steganography is often used in conjunction with encryption for additional security.
These four types of cryptography serve different purposes and are employed in various combinations to address different security requirements in modern systems and applications.
How do I enable Cryptography?
Enabling system cryptography typically involves configuring encryption settings or security features on your computer or device. The specific steps may vary depending on the operating system and the type of encryption you want to enable. Here’s a general guide for enabling system cryptography on different platforms:
Enable Cryptography for Windows
BitLocker:
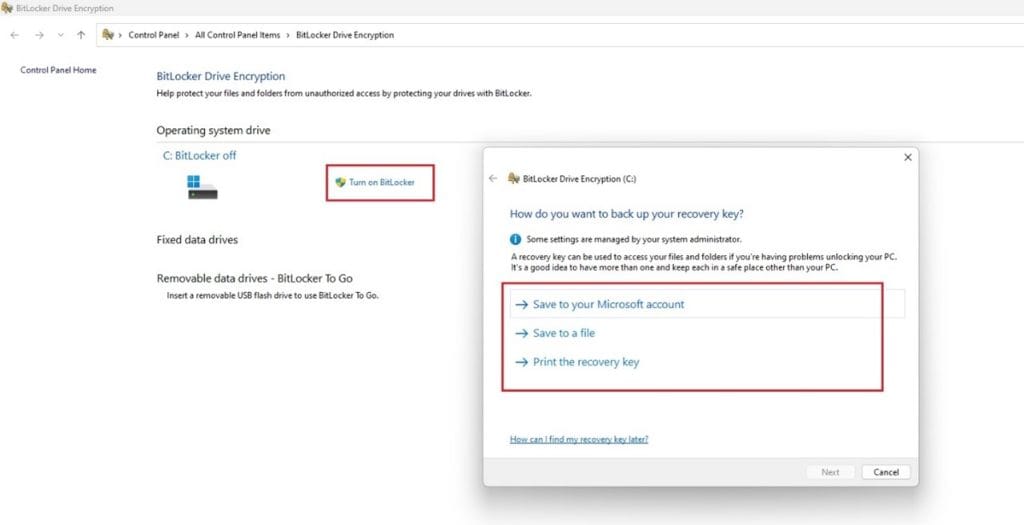
- Open the start menu and search for bit locker.
- Click on “Turn on BitLocker” next to the drive you want to encrypt and then use the appropriate method to save the recovery key.
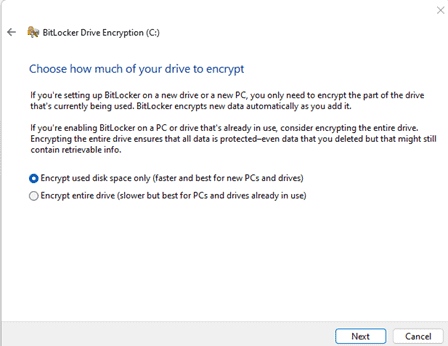
- Choose either you want to encrypt the whole drive or only the part that contains data.
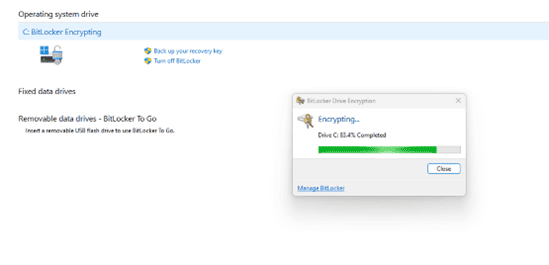
- The encryption will be started.
Enable Cryptography for Encrypting File System (EFS)
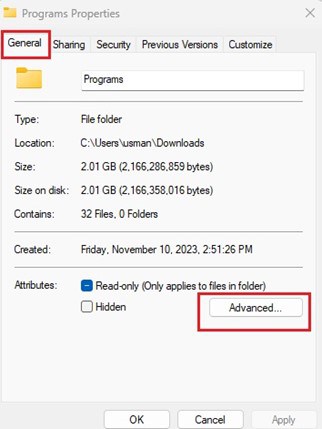
- Right-click on the file or folder you want to encrypt.
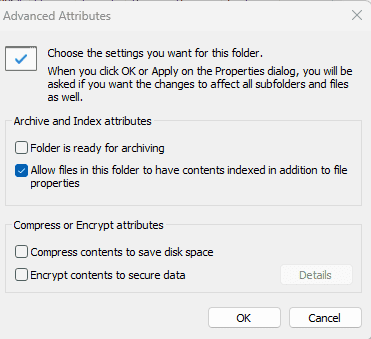
- Select “Properties” and then click on the “Advanced” button.
- Check the box next to “Encrypt contents to secure data” and click “OK.”
Enable Cryptography for Linux
LUKS (Linux Unified Key Setup):
LUKS is a standard for disk encryption used by many Linux distributions during installation. During the installation process, you’ll typically have the option to enable LUKS encryption for your disk partitions.
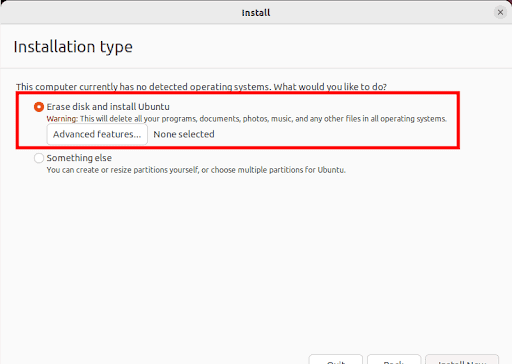
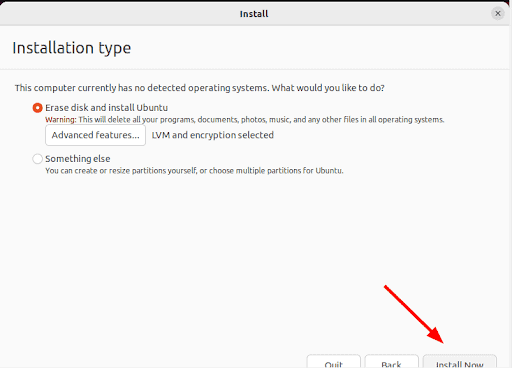
Fast forwarding the installation process, during the process two options will be presented. The first one (the default option) is "Erase disk and install Ubuntu" which wipes out all the existing data and automatically partitions the drive. The second option is "Something else" which is used to manually configure the disk partitions yourself. Please note that you will not be able to enable full disk encryption by selecting the second option.
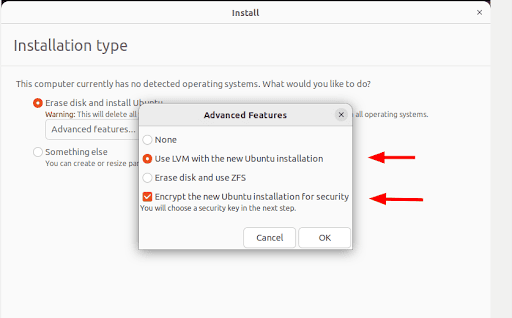
- Select the first option: "Erase disk and install Ubuntu" and click the "Advanced features" button.
- A pop-up will appear, be sure to select "Use LVM with new Ubuntu installation" and the "Encrypt the new Ubuntu installation for security" options and then click "OK."
- Next, assuming you have already backed up any important data, click "Install Now."
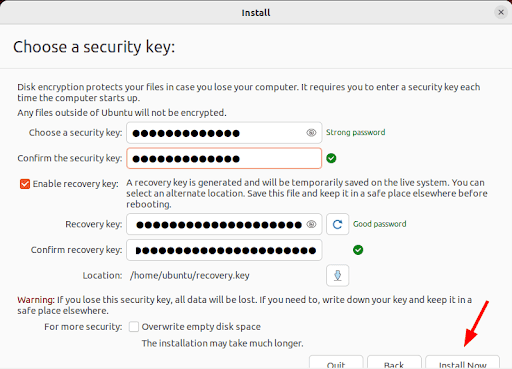
- Disk encryption requires a security key in order to access your files each time your device boots. In this step, provide a strong security key or passphrase. You can also enable a recovery key which enables a user to access the encrypted disk if they forget their password, or if the disk needs to be installed on a new device.
- Then click "Install Now."
- From here, continue with the installation process until the end, and finally, reboot the system. Provide the security key that you generated and hit ENTER prior to logging in.
Best Practice for Security Configurations
It’s best practice to leverage automated hardening tools when configuring security settings due to several key advantages. Automation ensures consistency and reduces the risk of human error during the configuration process. This is especially important when managing a large number of systems, where manual configuration can be time-consuming and error-prone. Additionally, automation allows for faster deployment of security updates and patches, keeping your systems protected against evolving threats. Overall, automated hardening streamlines the security process, improves accuracy, and ensures a more robust security posture.