What is an event in a Windows environment?
The Windows event log serves as a comprehensive and time-sequenced documentation of system, security, and application notifications. It’s maintained by the Windows operating system and utilized by network administrators for troubleshooting system issues and anticipating future challenges.
This systematic recording of various system and application activities in event logs provide a chronological record of events that occur on the system, offering invaluable insights into its operation and health.
Events can take the form of a variety of information including informational messages, warnings, errors, and audit trails. These events can encompass activities such as software installations, user logins, system startup and shutdown, hardware errors, security-related events, and much more.
What is command line in process creation events?
Basic event recording allows the administrator to know specific base layer information, for example if someone was trying to log into a device, it will record credentials such as username and password, and if the login attempt was successful or not.
The inclusion of command line in process creation events adds an extra layer of information to each event including details like the executable file being run, any arguments or parameters passed to it, and other relevant information.
This setting only applies to successful process creations. Failed attempts are not logged with the command line regardless of this setting’s state.
Benefits of command line in process creation events
Capturing process command line information in event logs can enhance threat detection, which can be valuable when performing forensic investigations of attack incidents. The more information recorded, the more likely the chances of an issue being caught and with greater speed.
The increased information recorded through the command line can be crucial when identifying suspicious activity through a number of means including: unmasking hidden behavior and patterns, detecting unauthorized actions and flagging them for investigation, and improving forensics through the reconstruction of events.
If not in possession of the extra layer of detail provided by command line, it might be impossible to define if use is malicious.
Considerations of command line in process creation events
Process command line information will be included in the event logs, which can contain sensitive or private information such as passwords or user data. If the correct access restrictions have not been set for the event logs, it is possible that this sensitive information can be accessed by unauthorized parties.
Another component to keep in mind is the size of the event logs, both virtually and in terms of storage. If too much information is recorded, more storage capacity will be necessary which could slow a system down or be costly. Alongside this, the more information gathered the longer it will take to process in the event of an investigation. Important information might also be obscured by the sheer amount of information being logged, reducing its effectiveness.
How to enable include command line in process creation events
To establish the recommended configuration via GP, set the following UI path to Enabled:
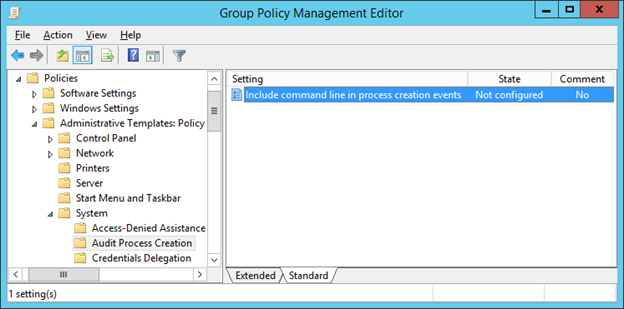
Computer Configuration\Policies\Administrative Templates\System\Audit Process Creation\Include command line in process creation events
Note: This Group Policy path may not exist by default. It is provided by the Group Policy template AuditSettings.admx/adml that is included with the Microsoft Windows 8.1 & Server 2012 R2 Administrative Templates (or newer).
Configuring inclusion of the command line in process creation events using a group policy
To configure inclusion of the Windows command line in process creation events using a group policy:
- Open the Windows Control Panel.
- Select Administrative Tools ? Group Policy Management.
The Group Policy Management Console is launched.
You can also launch the Group Policy Management Console by executing the gpmc.msc command. - In the left pane, select the node of the policy being used: Group Policy Management ? Forest: <forest name> ? Domains ? <Domain name> ? <Servers or workstations group policy name>.
- On the main menu, click Action ? Edit.
The Group Policy Management Editor window opens. - In the left pane, select the node Policy <policy name> ? Computer Configuration ? Policies ? Administrative Templates ? System ? Audit Process Creation.
- Select Include command line in process creation events.
7. On the main menu, click Action ? Edit.
8. In the window that opens, select Enabled.
9. Click OK.
Inclusion the Windows command line in process creation events is configured.
Group policy
Default: Not configured
Note: When this policy setting is enabled, any user with access to read the security events will be able to read the command line arguments for any successfully created process. Command line arguments can contain sensitive or private information such as passwords or user data.
Supported on: At least Windows Server 2012 R2, Windows 8.1 or Windows RT 8.1
CIS benchmark
Disabled. (The process’s command line information will not be included in Audit Process Creation events.)
Recommended state
The recommended state for this setting is: Enabled.
Note: This feature that this setting controls was not originally supported in workstation OSes older than Windows 8.1. However, in February 2015 Microsoft added support for the feature to Windows 7 and Windows 8.0 via an update – KB3004375. Therefore, this setting is also important to set on those older OSes
Event Log Hardening
Event logging is a great tool to deploy in the event of an attack, but it is always better to harden a system to prevent attacks from occurring in the first place. Server hardening is paramount for upholding the security of a system, providing an excellent defense from those wishing to gain unauthorized access into a system.