Requiring user authentication by using NLA is only a small step towards achieving a hardened Remote Desktop Server. Server hardening can be a painful procedure. If you're reading this article, you probably already know it. Endless hours, labor, and money are invested in this process, which can often result in production breakdown despite the effort to prevent it. CHS by CalCom automates the entire server hardening process. CHS's unique ability to 'learn' your network eliminates the need to perform lab testing while ensuring zero outages to your production environment. CHS will allow you to implement your policy directly on your production servers, hassle-free.
In this article you'll learn:
- The role of NLA connection
- The potential vulnerability in this rule
- How to mitigate this vulnerability
- The potential impact of mitigating it on your network's function
- The severity of the vulnerability
- What we recommend to do
- A practical guide on how to configure this setting in the most secure fashion
POLICY DESCRIPTION:
This policy setting allows you to specify whether to require user authentication for remote connections to the RD Session Host server by using Network Level Authentication (NLA). This policy setting enhances security by requiring that user authentication occur earlier in the remote connection process. If you enable this policy setting, only client computers that support Network Level Authentication can connect to the RD Session Host server. To determine whether a client computer supports Network Level Authentication, start Remote Desktop Connection on the client computer, click the icon in the upper-left corner of the Remote Desktop Connection dialog box, and then click About. In the About Remote Desktop Connection dialog box, look for the phrase “Network Level Authentication supported". If you disable or do not configure this policy setting, Network Level Authentication is not required for user authentication before allowing remote connections to the RD Session Host server. You can specify that Network Level Authentication be required for user authentication by using the Remote Desktop Session Host Configuration tool or the Remote tab in System Properties.
POTENTIAL VULNERABILITY:
When using RDP with NLA disabled or not configured, remote users can access the RDP tunnel without any authentication required. This dramatically increases the chance for attackers to perform RDP based attacks, such as the wormable BlueKeep among others. Enabling NLA will block attackers lacking authentication credentials, and it is recommended specifically for BlueKeep prevention, regardless of patching actions.
COUNTERMEASURES:
Enable 'Require user authentication for remote connections by using Network Level Authentication.
POTENTIAL IMPACT:
- Enabling NLA will allow only authenticated users to establish a session to a remote desktop server, therefore it will not support any other credentials providers.
- NLA requires an "access this computer from the network" privilege, which might be restricted.
- It is not possible to change the password via CredSSP, which creates a problem when 'User must change password at next logon' is enabled or if an account's password expires.
- The users who’re trying log on password will not be stored in the security audit logs, making it harder for a firewall to block brute force or directory attacks.
- Client's computer must use at least Remote Desktop Connection 6.0.
- The client's computer must be using a modern OS such as Windows 7.
- The Remote Desktop Session Host server must be running Windows Server at least 2008 R2 or Windows Server 2008.
- The RDS client must be running Windows XP SP3 or later.
SEVERITY:
Critical
CALCOM’S RECOMMENDED VALUE:
Enable
HOW TO CONFIGURE:
The next example will show how to configure a GPO for NLA authentication for RDP.
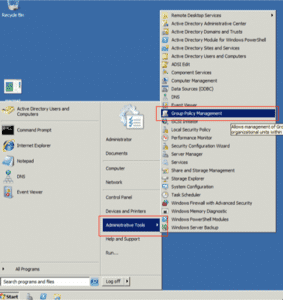
- Select from Administrative Tools the Group Policy Management tool:
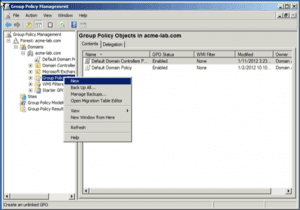
2. On the tool, create a New Group Policy Object:
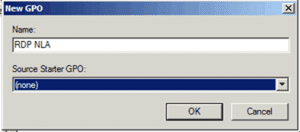
3. Give this policy a Name:
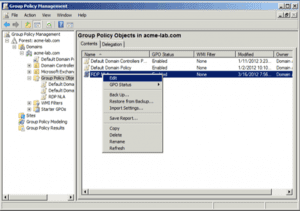
4. Edit this policy by right-clicking on it and selecting Edit:
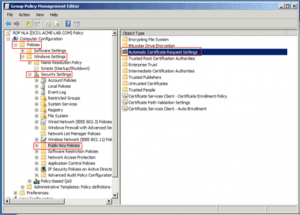
5. Select Computer Configuration/Policies/Windows Settings/Public Key Policies/Automatic Certificate Request Settings:
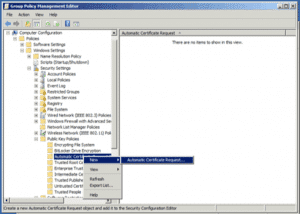
6. Right-click on Automatic Certificate Request Setting and select to create a new Automatic Certificate Request, this will request to the CA a new Computer Certificate and renew the certificate when it expires automatically.
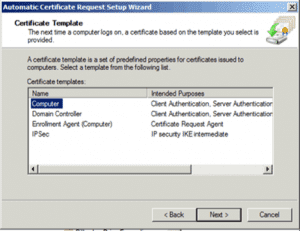
7. When the wizard starts, click Next then select Computer Certificate Template:
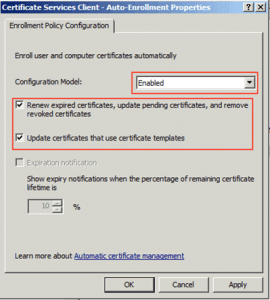
8. Click on Next and then on Finish. Now, select Computer Configuration/Policies/Windows Settings/Public Key Policies under that node double click on Certificate Services Client - Auto-Enrollment and select on the properties under Configuration Model select Enabled and make sure that the boxes for managing certificates in the store and for updating the certificate if the template is modified.
Now we have finished the section that will cover the certificate assignment for computers that get this GPO applied to.
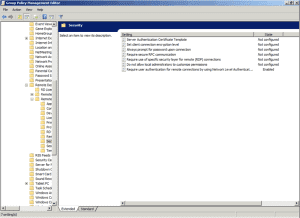
9. For configuring RDP to use NLA we now go to Computer Configuration/Policies/Administrative Templates/Windows Components/Remote Desktop Settings/Remote Desktop Session Host/Security
10. Select Require user authentication for remote connections by using Network Level Authentication and double click on it. On the properties screen select Enable and click on