In 2014 and with extensive community involvement NIST Cybersecurity Framework was created for private sector organizations in the United States. It is also aligned with other NIST standards and guidelines, such as NIST 800-53 and FedRAMP. NIST Cybersecurity Framework (CSF or Framework) is intended to be a living document that is refined and improved over time and was updated in 2018 and called CSF 1.1. We will be discussing NIST CSF 2.0.
The statutory authority for the CSF directs NIST to "facilitate and support the development" of the Framework and "coordinate closely and regularly" with relevant organizations. This means CSF is being updated in an open manner with input from government, academia, and industry, including through workshops, public review and comment, and other forms of engagement.
On January 19, 2023 NIST published a concept paper to seek additional input on the structure and direction of the Cybersecurity Framework before crafting a draft called Cybersecurity Framework 2.0 (CSF 2.0.). NIST Cybersecurity Framework 2.0 Concept Paper: "Potential Significant Updates to the Cybersecurity Framework," version will reflect the evolving cybersecurity landscape.
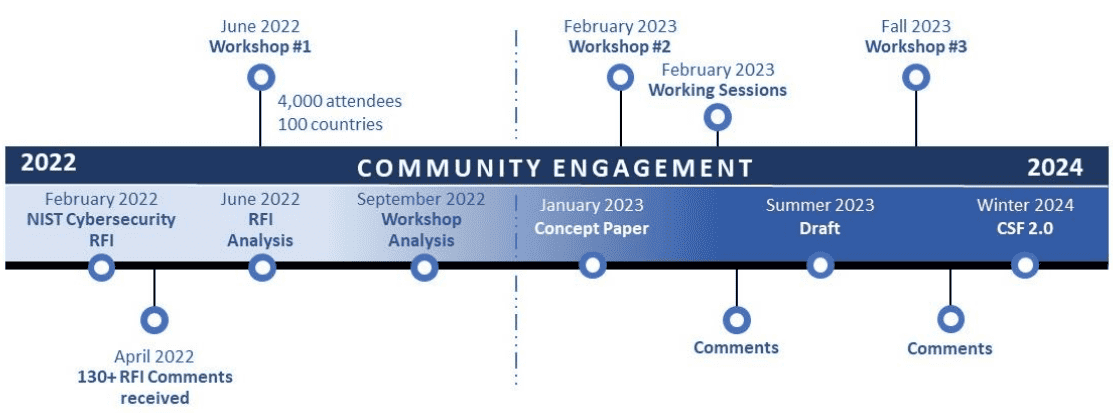
An initial CSF 2.0 timeline is shown in this figure:
Let's review the potential Significant Changes in CSF 2.0 as it's been outlined in the NIST Cybersecurity Framework 2.0 Concept Paper. Note that NIST states "This paper does not cover all potential changes that may be made to the Framework structure, format, and content, especially specific changes to Categories and Subcategories of the CSF Core."
Potential Significant Changes in CSF 2.0
1. CSF 2.0 will explicitly recognize the CSF's broad use to clarify its potential applications.
1.1. Change the CSF's title and text to reflect its intended use by all organizations
CSF 2.0 will employ the broader and commonly used name, "Cybersecurity Framework" instead of the original "Framework for Improving Critical Infrastructure Cybersecurity."
The scope of CSF 2.0 will cover all organizations across government, industry, and academia, including but not limited to critical infrastructure.
1.2. Scope the CSF to ensure it benefits organizations regardless of sector, type, or size
CSF is a recognized resource for state and local organizations under the Department of Homeland Security (DHS) State and Local Cybersecurity Grant Program and has been referred to widely by many associations as well as government agencies at multiple levels.
NIST will increase its efforts to ensure the Framework is helpful to organizations - regardless of sector, type, or size - in addressing cybersecurity challenges and encourages all interested parties to participate in the process.
1.3. Increase international collaboration and engagement
NIST will prioritize exchanges with foreign governments and industry as part of CSF 2.0 development. NIST will continue to engage directly and through interagency partnerships to share the benefits of CSF use, as well as to solicit input on potential changes so that the CSF can continue to be recognized as an international resource.
NIST will also prioritize working with organizations to develop translations of CSF 2.0 in conjunction with its development.
2. CSF 2.0 will remain a framework, providing context and connections to existing standards and resources
2.1. Retain CSF's current level of detail
NIST aims to maintain the current level of detail and specificity in CSF 2.0 to ensure it remains scalable and flexible for a wide range of organizations.
2.2. Relate the CSF clearly to other NIST frameworks
Other NIST cybersecurity- and privacy-related frameworks will remain separate frameworks as they individually focus on specific topics worthy of dedicated guidance.
However, each framework (i.e. Privacy Framework, Risk Management Framework) has a relationship with the CSF, so they will be referenced as guidance either in CSF 2.0 or in companion materials, such as mappings.
2.3. Leverage Cybersecurity and Privacy Reference Tool for online CSF 2.0 Core
In addition to PDF and Excel formats, the newly launched NIST Cybersecurity and Privacy Reference Tool (CPRT) will showcase CSF 2.0. CPRT provides a standardized machine-readable format and user interface for accessing reference data from NIST cybersecurity and privacy standards, guidelines, and frameworks. It also offers a versatile method for describing the connections between standards, guidelines, frameworks, applications, and technology.
2.4. Use updatable, online Informative References
In CSF 2.0, NIST will move toward the use of online, updatable references showcased through CPRT
2.5. Use Informative References to provide more guidance to implement the CSF
NIST will work with the community to encourage and enable the production of mappings that support CSF 2.0. By utilizing online resources, the CSF can be linked to more targeted references to offer supplementary recommendations. For instance, it can provide guidance on securing controlled unclassified information, cloud computing, Internet of Things (IoT) and operational technology (OT) cybersecurity, zero trust architecture (ZTA), and other related areas. The use of an online format can also allow mappings with a greater description of the relationship between resources currently included in the CSF Core.
2.6. Remain technology- and vendor-neutral, but reflect changes in cybersecurity practices
NIST will work to review the CSF so that its broad outcomes can continue to be leveraged by organizations regardless of the technology or services they employ, including IT, IoT, OT, and cloud services.
3. CSF 2.0 (and companion resources) will include updated and expanded guidance on Framework implementation
Many would benefit from straightforward, more general descriptions of the Framework's key components, while others request detailed information such as linkages and mappings to specific cybersecurity guidance from NIST and other organizations. In conjunction with the development of CSF 2.0, NIST will address both needs using several approaches.
3.1. Add implementation examples for CSF Subcategories
To ensure the CSF Core remains high-level and concise, there would be a small number of notional examples. This small list of examples would not be a comprehensive list of all actions that could be taken by an organization to meet CSF outcomes, nor would they represent a baseline of required actions to address cybersecurity risks.
Adding examples can help clarify the meaning and intent of each Subcategory and provide high-level implementation ideas with the CSF Core for those less familiar with the detailed cybsersecurity standards. They may also address the evolving nature of cybersecurity technologies and techniques by highlighting possible differences in implementations for platforms.
3.2. Develop a CSF Profile template
NIST will produce an optional basic template for CSF Profiles suggesting a format and areas to be considered in Profiles. While organizations may continue to use different formats for Profiles based on their specific needs, use of a template is expected to increase the production of sector and organization-specific Profiles and make the development of Profiles easier for users.
3.3. Improve the CSF website to highlight implementation resources
The update to the Framework presents an opportunity to increase awareness of existing resources NIST already has to offer such as CSF sample Profiles, mappings, guidance, tools, case studies, success stories, related publications, etc…as well as to identify new ones.
4. CSF 2.0 will emphasize the importance of cybersecurity governance
Cybersecurity governance is currently addressed in CSF 1.1 in the "Identify" Function, as well as in the section on "How to Use the Framework." CSF 2.0 will expand the consideration of these topics.
4.1. Add a new Govern Function
CSF 2.0 will include a new "Govern" Function to emphasize cybersecurity risk management governance outcomes.
This new crosscutting Function will highlight that cybersecurity governance is critical to managing and reducing cybersecurity risk. The new Govern Function in CSF 2.0 will inform and support the other 5 Functions.
4.2. Improve discussion of relationship to risk management
CSF 2.0 will describe how an underlying risk management process is essential for identifying, analyzing, prioritizing, responding to, and monitoring risks, how CSF outcomes support risk response decisions, and various examples of risk management processes (e.g., Risk Management Framework, ISO 31000) that can be used to underpin CSF implementations.
5. CSF 2.0 will emphasize the importance of cybersecurity supply chain risk management (C-SCRM)
5.1. Expand coverage of supply chain
Managing cybersecurity within the supply chain was one of the key additions in the last update to the CSF. NIST believes CSF 2.0 should include additional Cybersecurity Supply Chain Risk Management (C-SCRM) specific outcomes to provide additional guidance to help organizations address these distinct risks.
6. CSF 2.0 will advance understanding of cybersecurity measurement and assessment
Measurement and assessment of cybersecurity risk management programs and strategies continue to be an important area in the use of the CSF.
A related desire for the CSF is to clearly explain how organizations can use the Implementation Tiers, and how they relate to measurement.
6.1. Clarify how leveraging the CSF can support the measurement and assessment of cybersecurity programs
CSF 2.0 will make clear that by leveraging the CSF, organizations have a common taxonomy and lexicon to communicate the outcome of their measurement and assessment efforts, regardless of the underlying risk management process.
6.2. Provide examples of measurement and assessment using the CSF
Because there is no single approach to measure and assess the CSF, NIST will not put forward a single approach to assessment in the CSF 2.0 in order to continue flexibility in how organizations may implement the Framework. CSF 2.0 will include examples of how organizations have used the CSF to assess and communicate their cybersecurity capabilities.
6.3. Update the NIST Performance Measurement Guide for Information Security
NIST is updating its flagship measurement guidance document, the ‘Performance Measurement Guide for Information Security.’
6.4. Provide additional guidance on Framework Implementation Tiers
CSF 2.0 will clarify the scope and applicability of Tiers to address robustness of risk management processes, programs, and external communication. The update will also better describe the relationship between Tiers and maturity model concepts. CSF 2.0 will not provide a distinct maturity model to meet CSF outcomes at the Function, Category, or Subcategory level.
Learn More about NIST Cybersecurity Framework 2.0 Concept Paper: "Potential Significant Updates to the Cybersecurity Framework,"