What is credential validation?
In any system, it’s important to know who is trying to gain access, whether successful or not. This is especially important when trying to keep something secure, like a network or confidential data.
Ensure ‘Audit Credential Validation’ is set to ‘Success and Failure' keeps track of attempts to access a system, whether successful or not, using specific credentials, such as a username and password, and logs it.
The process of credential validation starts with checking the credentials, i.e. the username and password are correct and match. The next step is to log this information in the security log, which will happen in different locations depending on the system. If logging in to a network, these checks are conducted and logged by the domain controller. If using a personal computer these checks are done by the computer locally.
Each log on attempt is referred to as an 'event', and for each event there is a subcategory and code, including:
- 4774: (Success, Failure) An account was mapped for logon.
- 4775: (Failure) An account could not be mapped for logon.
- 4776: (Success, Failure) The Domain Controller attempted to validate the credentials for an account.
- 4777: (Failure) The Domain Controller failed to validate the credentials for an account.
Why correctly logging credential validation is important
Logging credential validation attempts is helpful to see if there are any suspicious login attempts being made in a system. For example if someone is attempting to log in with an incorrect password it will be recorded, and if they do manage to get into the system this will be recorded too.
Having a list of these events helps to identify suspicious activity and potential attack attempts improving the systems overall security posture. This monitoring also helps to identify unusual patterns that could be malicious activity and allows it to be double checked before an attack may occur.
Giving IT the ability to go back through previous events allows them to conduct network forensic analysis, investigating incidents after the fact, giving them the ability to better understand what happened and how to bolster the system security.
How secure is too secure for credential validation
In the event of an attack, if the audit settings are configured to be too lax, the incident might not be detected, or if detected, not enough evidence recorded for network forensic analysis to be conducted.
However, if audit settings are too strict, critically important entries in the security log may be lost bythe IT staff being overwhelmed by all the meaningless entries recorded. This can also have an effect on data storage, clogging the system with irrelevant information.
Finding the correct balance is imperative for correctly securing a system. Additionally, some companies working in specific regulated industries may have legal obligations to log certain events or activities.
Setting Audit Credential Validation via Group Policy
To establish the recommended configuration via GP, set the following UI path to Success and Failure:
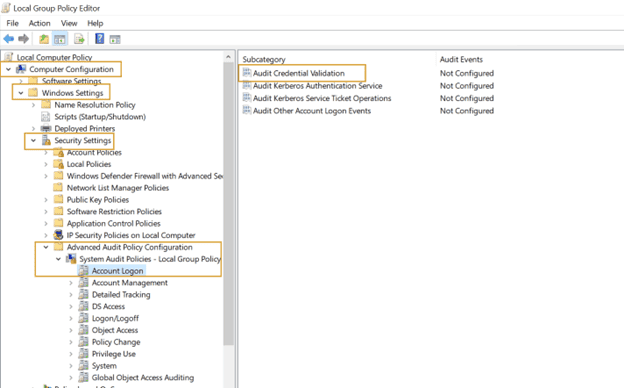
Computer Configuration\Policies\Windows Settings\Security Settings\Advanced Audit Policy Configuration\Audit Policies\Account Logon\Audit Credential Validation
Or by following this procedure:
- Launch Server Manager in your Windows Server instance.
- Under Manage, select Group Policy Management and launch the Group Policy Management console.
- Navigate to Forest ? Domain ? Your domain ? Domain Controllers.
- Create a new GPO and link it to the domain containing the file to be monitored, or edit any existing GPO that is linked to the domain to open the Group Policy Management Editor.
- Navigate to Computer Configuration ? Windows Settings ? Security Settings ? Advanced Audit Policy Configuration ? System Audit Policies – Local Group Policy ? Account Logon.
- The Account Logon lists all of its sub-policies in the right panel, as shown in the figure below.
- Select the Audit Credential Validation and enable audit for Success and Failure events.
- Click Apply and OK to close Properties window.
Recommended settings
The recommended state for this setting is: Success and Failure.
Default value
The default value for this setting is: Success.
Configuration Best Practices
Incorrect configuration of Audit Credential Validation settings will not directly lead to vulnerabilities, but it can lead to reducing the security posture of a system. Not being able to detect malicious patterns can expose a system to a number of known threats such as credential stuffing, account enumeration, brute force attacks, insufficient logging and misconfiguration authentication mechanisms to name a few.
For these reasons it is essential to properly harden your system, mitigating attack surfaces and making it quicker to detect and respond to thr