What is anonymous access?
Windows permits an anonymous user to carry out specific actions, such as listing the names of domain accounts and network shares. This functionality proves useful in scenarios when an administrator needs to provide access to users in a trusted domain lacking a reciprocal trust agreement.
By default, the Everyone security identifier (SID) is excluded from the token generated for anonymous connections. Consequently, permissions assigned to the Everyone group don’t extend to anonymous users. Enabling this option restricts anonymous users to accessing only those resources for which explicit permission has been granted to them.
Network access: Let Everyone permissions apply to anonymous users
This policy setting determines the extra permissions allocated for anonymous connections to the computer. When enabled, anonymous users possess identical rights and permissions to those in the built-in Everyone group. However, it’s important to note that granting such permissions to anonymous users is discouraged.
Default Settings
The table below showcases both the actual and effective default values for Network access Let Everyone permissions apply to anonymous users:
| Server type or GPO | Default value |
| Default Domain Policy | Not defined |
| Default Domain Controller Policy | Not defined |
| Stand-Alone Server Default Settings | Disabled |
| DC Effective Default Settings | Disabled |
| Member Server Effective Default Settings | Disabled |
| Client Computer Effective Default Settings | Disabled |
Disable setting for anonymous user
This corresponds to the following Windows Server registry options. To restrict anonymous users:
| Registry Hive | HKEY_LOCAL_MACHINE |
| Registry Path | \System\CurrentControlSet\Control\Lsa\ |
| Value Name | EveryoneIncludesAnonymous |
| Value Type | REG_DWORD |
| Default Value | 0 |
Configure the policy value for Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options -> “Network access: Let everyone permissions apply to anonymous users” to “Disabled”.
The step-by-step instructions are:
- Start the registry editor (regedit.exe)
2. Scroll to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa
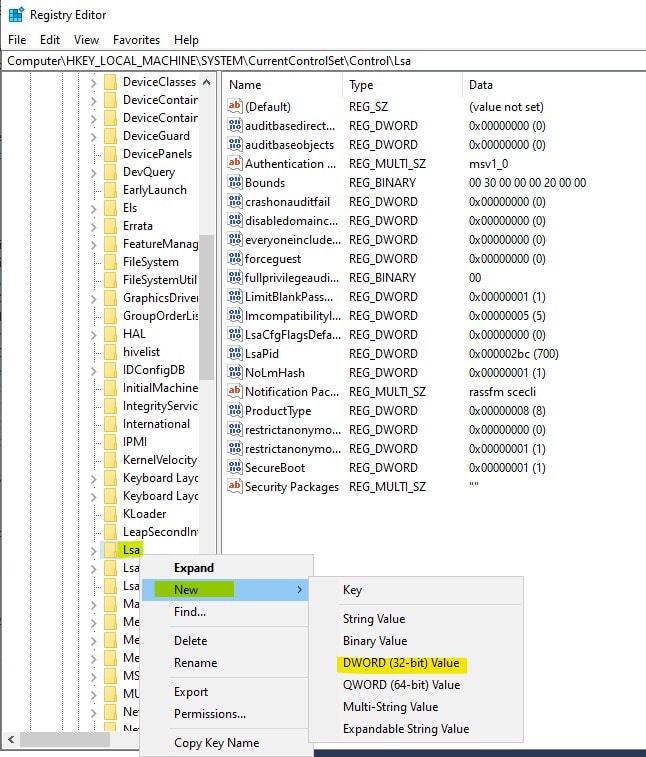
3. Right click, from the Edit menu select New – DWORD value and enter a name of EveryoneIncludesAnonymous if it does not already exist
4. Double click the value and set to 0. Click OK
5. Reboot the computer
Vulnerabilities with anonymous user
An unauthorized user could anonymously list account names and shared resources and use the information to attempt to guess passwords, perform social engineering attacks, or launch DoS attacks.
Best Practices for anonymous user
Configure the Let Everyone permissions apply to anonymous users setting to Disabled.
Automating the configuration of the setting enhances operational efficiency, strengthens security, and ensures regulatory compliance within an organization’s network infrastructure.
To configure remediation for the setting:
Audit:
Navigate to the UI Path articulated in the Remediation section and confirm it is set as prescribed. This group policy setting is backed by the following registry location:
| HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa:EveryoneIncludesAnonymous |
Remediation:
To establish the recommended configuration via GP, set the following UI path to Disabled:
| Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Security Options\Network access: Let Everyone permissions apply to anonymous users |
Default Value:
Disabled. (Anonymous users can only access those resources for which the built-in group ANONYMOUS LOGON has been explicitly given permission.)