On March 2020 Microsoft published a patch that supposes to help prevent unsigned LDAP channel binding attacks on Domain Controllers (DC). In this article, we'll dive into the attack and what you should know before patching in order to prevent production outages.
What is channel binding:
Channel binding is the process of binding the application and transport layers together. In the specific case of LDAP channel binding, the transport layer is the TLS tunnel that being tied with the LDAP application. The main use of this process is to ensure trusted communication between the client and the DC. Tying the two layers together creates a unique fingerprint, that can't be reused, of the LDAP communication. This communication can't be duplicated, because establishing a new TLS tunnel will change the LDAP communication's fingerprint.
What is LDAP Singing:
LDAP signing is the digital signing of the source of the traffic to the LDAP communication. This digital signing guarantees that the traffic hasn't been altered in the transit, and verifies the origin of this LDAP traffic. Note that LDAP signing must be configured on both the DCs and the users.
What kind of attacks can be performed using unsigned LDAP channel binding:
There are two types of attacks that leverage unsigned LDAP channel binding-
-
Pass-The-Ticket attack:
Pass the ticket attack is a method of impersonating users on a DC. The attacker captures a TGT ticket and uses it to impersonate the user. the ticket is valid for a period of time (10 hours default) and can be used to request more tickets. When using an unsigned LDAP, the traffic source is not verified, allowing the attacker to access the DC.
-
Man-In-the-Middle attack:
In MItM attacks the attacker captures the LDAP packet sent from the client to the DC, adding it a malicious code that will affect the DC. When using unsigned LDAP traffic, there's no way to verify that the traffic hasn't been altered before it arrived at the DC.
Preventing LDAP Reconnaissance- The First Step of AD Attacks
How Can You Mitigate These Attacks:
In order to mitigate these attacks, DC must require LDAP signing. In order to do it you must configure DC 'Domain Controller: LDAP server signing requirements' to 'require signing'. Domain member computers must be configured in 'Network Security: LDAP signing requirements' to 'Negotiate signing' or higher.
Microsoft March 2020 Update for LDAP Channel Binding and Signing:
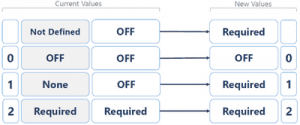
In March 2020 Microsoft published an update and declared that LDAP singing and channel binding are mandatory. The patch changed the configuration values either 'OFF' or 'Required'. The default value is 'Required'. In this status, you won't be able to use Simple Binding and Unsigned SASL Activity.
According to the CIS Benchmarks, requiring LDAP signing will damage your servers' functionality if you use TLS/SSL, if you have low-level clients or non-Microsoft OS. But there are few other scenarios when you should consider not updating:
- If you use legacy applications that won't necessarily support this update
- Java applications
- Storage that uses LDAP traffic to connect the DC
How can you know if you can require LDAP channel binding signing:
Understanding the real impact of this configuration change is complex and requires tests to be initiated on test environment. This means a lot of time and effort to invest. CalCom hardening automation tool- CHS will eliminate the need to perform any kind of testing. CHS will learn your production and report you on the possible impact of every configuration change. It will then implement the desired change on your entire production from a single control point, so you won't have to use GPOs or do it manually. Learn more about CHS by downloading our datasheet.