Defining and implementing a comprehensive server security policy is an essential step in the process of securing both Windows and Linux servers. Organizations should establish different hardening policies for each system component, aspiring to be as granular as possible (differentiating component's type, role, version, environment, etc.). System hardening has become a mandatory requirement in every regulation and by implementing a good hardening policy set by best practices from organizations such as CIS Benchmarks and DISA STIG reduces the risk of vulnerabilities and breaches
System hardening refers to actions done to reduce the attack surface, by securing the configurations of the system's components (servers, applications, etc.). As arrived from the manufacturer, system components are more function-oriented than secure, which means that unnecessary functions are enabled.
After establishing a hardening policy there are 3 stages you must complete to achieve baseline hardening:
1. Testing - pushing your policy as is on to your system will cause extensive damage. While hardening best practices instruct to disable and block any potential attack vector, some rules just cannot be implemented since these settings are in use. To understand which rules can and can not be enforced, you must understand the entire dependencies in your network. The practice of the testing stage is building a test environment that will simulate your network as accurately as possible and test the impact of each rule enforcement on it. This is, by all means, the hardest, longest, and most resource-demanding stage of the hardening project. In addition, it is the most important one, since if not done properly, it will result in production outages.
After finishing testing each configuration change's impact, the policy must be discussed again to decide the course of action of each impacting rule.
2. Enforcing - after testing and adjusting the policy to the test's findings, you'll need to enforce all policies on all system components. This stage is also highly prone to human mistakes if you are no using assistive tools. Ensure all components have been enforced with the right policy, and that all policy rules have been properly pushed has high management complexity.
3. Monitoring - if you do not want to get back to square one in your compliance posture, monitoring is essential. The organizational network is dynamic and constantly changes. New applications are installed, old machines die, and you must have the ability to react to these changes, so you won't lose your compliance posture. In addition, changes in configuration can occur either intentionally or unintentionally, and you must have the ability to monitor and fix them.
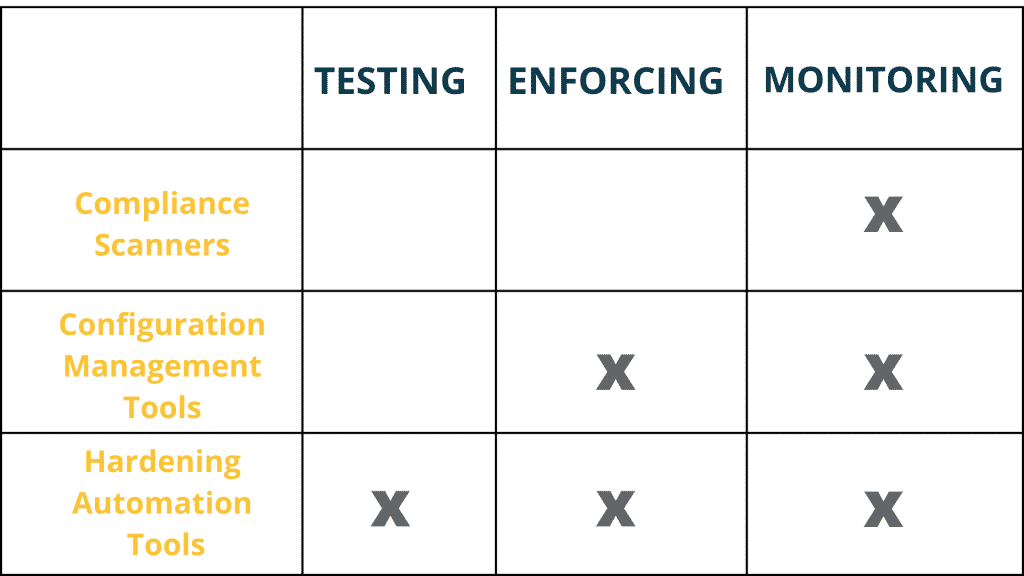
There are 4 groups of tools to check before a hardening project is to begin:
- Compliance scanners
- Configuration management tools
- Hardening automation tools
- Free open-source tools
Each type of tool offers a solution for a different stage in the hardening project:
Compliance scanners:
Features: Monitoring
Description: Compliance scanning focuses on assessing adherence to a certain compliance framework (e.g. CIS Benchmark, DISA STIG). Compliance scanners produce a report indicating how well a system is hardened comparing to a compliance framework.
Tools:
- Tripwire Configuration Manager – gives you the ability to view all your assets’ configuration and compliance status of all your assets in a single reporting environment.
- Qualys - provides configuration scanning and simplifies workflows to address configuration issues.
- NNT SecureOps - provides intelligence change control and automation. Audits and automates continuous compliance. Provides real-time detection for suspicious changes.
- CIS-CAT Pro – CIS-CAT® Pro Assessor evaluates the cybersecurity posture of a system against recommended policy settings. The tool helps organizations save time and resources by supporting automated content with policy-setting recommendations based on the globally recognized CIS Benchmarks.
Configuration management tools:
Features: Enforcing, Monitoring.
Description: according to NIST, security configuration management (SCM) can be described as "The management and control of configurations for an information system with the goal of enabling security and managing risk."
By using SCM tools you'll be able to:
- Enforce your desired policy, enabling you to configure your infrastructure to your desired state
- Easily enforce configuration changes throughout the infrastructure from a single point of control
- Choose the version you're working with
- Easily make changes in code
- Keep track of what changes were made and who changed them
- Approve or reject changes request
- Reporting and recording the configuration status
Tools:
- Ansible - Ansible is a RedHat platform allowing the user to control and develop automation in the IT network. It is not specific for hardening but can be used for that.
- Chef – Chef Enterprise Automation Stack (EAS) provides teams implementing DevSecOps with a common approach for automating application delivery, infrastructure configuration, and compliance auditing. It is not specific for hardening but can be used for that.
- Puppet - open-sourced powered infrastructure automation platform. It is not specific for hardening but can be used for that.
- Microsoft System Center Configuration Management - Microsoft Configuration Manager that provides remote control, patch management, software distribution, operating system deployment, network access protection, and hardware and software inventory. It is not specific for hardening but can be used for that.
- SolarWinds Network Configuration Manager - features network compliance, network automation, configuration backup, and vulnerability assessment.
Hardening automation tools:
Features: Testing, Enforcing, Monitoring.
Description: hardening automation tools offer a complete hardening solution. They transform this tangled process into a ‘click-of-a-button’ task. Using hardening automation tools you won’t need to write a single script or have any specific expertise.
They perform the entire testing procedure automatically by learning your infrastructure’s dependencies and reporting the potential impact of each configuration change. Only this feature alone can save most of the time and resources invested in the hardening project, making hardening automation tools preferable in terms of ROI.
Following the testing phase, hardening automation tools will also implement your policy on your entire production, using a single point of control. This dramatically eases the enforcement task and lowers the possibility of human errors to a minimum. The entire configuration orchestration procedure is easy and controlled from a single point of control.
Finally, hardening automation tools will monitor your network and remediate any undesired changes in compliance posture. It will alert and correct configuration drifts and be reactive to structural changes of the network (setting up new machines, or killing old ones). This will promise to preserve your compliance posture.
Hardening automation tools have all the capabilities of Security Configuration tools and Compliance Scanners in addition to the capability to perform impact analysis.
Tools:
- CalCom Hardening Automation Solution– CalCom Hardening Automation Suite (CHS) is a hardening automation platform designed to reduce operational costs and increase infrastructure’s security and compliance posture. CHS eliminates outages and reduces hardening costs by automating every stage in the hardening process:
1. Automatic impact analysis: indicating the impact of a security hardening change on the production services.
2. Automatic policy implementation: after setting a policy according to the impact analysis report, CHS will implement each policy on the right machine from a single point of control.
3. Continues compliance – CHS will monitor your compliance posture, alert, and remediate configuration drifts.CHS will ensure your compliance level remains high in the dynamic ever-changing infrastructure, so you won’t need to perform hardening from scratch a few months post your initial hardening project.
Open-source hardening tools:
- Salt Project – Its automation, infrastructure management, its data-driven orchestration, remote execution, configuration management.
- Microsoft Security Compliance Toolkit 1.0 – a set of tools that allows enterprise security administrators to download, analyze, test, edit and store Microsoft-recommended security configuration baselines for Windows and other Microsoft products while comparing them against other security configurations.
- Hardening auditor– Scripts for comparing Microsoft Windows compliance with the ASD 1709 & Office 2016 Hardening Guides.
- Windows Exploit Suggester Next Generation – WES-NG is a tool based on the output of Windows’ systeminfo utility which provides the list of vulnerabilities the OS is vulnerable to, including any exploits for these vulnerabilities. Every Windows OS between Windows XP and Windows 10, including their Windows Server counterparts, is supported.
- Privesc – Windows PowerShell script that finds misconfiguration issues which can lead to privilege escalation.
- Windows-privesc-check – Windows-privesc-check is a standalone executable that runs on Windows systems. It tries to find misconfigurations that could allow local unprivileged users to escalate privileges to other users or to access local apps (e.g. databases).