The Ryuk ransomware operators continue to target hospitals despite the Corona Virus and the massive loads they have to cope with.
According to BleepingComputer, only two of the ransomware groups they've contact with, have responded that due to the pandemic, they won't be targeting any hospitals or other healthcare facilities.
Emotet, TrickBot & Ryuk Attack Can Be Mitigated With Hardening
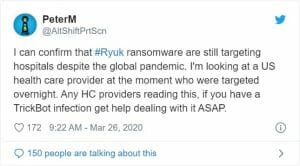
Ryuk ransomware group hasn't responded to BleepComputer. Furthermore, Ryuk attacks constantly being reported by hospitals and healthcare providers. For example, only a few days ago Ryuk attack on a US healthcare provider was reported. Their data was encrypted by what "looks like as typical Ryuk attack at the moment" (PeterM).
10 more attacks on hospitals were reported only in the last month, some of them already failing under the pandemic load.
Encrypting a hospital's data affects the ability of the doctors to provide the proper healthcare and with no doubt risk human lives.
Ryuk ransomware usually uses other trojans to inject itself into the system. Recently, the most common trojans used by Ryuk are Emotet and TrickBot.
Hospitals are now required to take quick actions to minimize the risk of this attack, as they can't afford any disruptions in their function.
Here are CalCom's recommendations for hardening actions that will minimize the chances for Ryuk attack based on Emotet and TrickBot:
- Restrict the use of system administration tools such as PsExec. Only use tools that admins need.
2. Disable unnecessary services, i.e., RDP/terminal services.
3. Ensure logging is enabled wherever possible- Reviewing logs to search for errors, anomalies or suspicious activity that deviates from the norm.
4. Ensure PowerShell logging and security by limiting and hardening PowerShell usage, logging trusted PowerShell processes and remove remote invoke.
5. Activate Software Restriction Policy (SRP) in a pinpoint:
SRPs identifies software programs running on computers in a domain. SRFs controls the ability of those programs to run, including specific file path locations, e.g., %APPDATA% directory in the user profile. Software restriction policies are part of the Microsoft security and management strategy and CIS recommendations.
6. Disable and remove SMB v1 and SMB v2in your environment.
7. Disable and remove old authentication protocols such as LM & NTLM 1.
8. Restrict RDP/terminal services on all levels. Enforce best practice secure configuration:
*limit connections.
*limit devises redirection.
*use network-level authentication and limit authentication types.
*limit RDP groups and RDP user's rights assignment authorizations.
9. configure Tunneling Remote Desktop connections through IPSec or SSH.
10. Restrict privileged and service account on an OS per server per role bases.
11. Disable local hash saving and control the server's credential manager.
12. Harden your servers based on CIS benchmarks and CIS controls.
13. Configure and harden your Active Directory/Domain Controllers more securely.
How CHS automates your hardening process and protects your organization:
Recovering from having your entire data encrypted, including your backups sounds almost impossible, but a lot can be done to prevent this situation from happening. Although some of the actions, such as disabling SMB, sounds straight forward, implementing them consumes time and effort and often don't prevent the unwanted outcome of production damage.
CHS can save you all this headache. CHS learns your environment and maps it. It is then implementing your desired policy, defined by either your organization or based on best practices such as the CIS benchmarks without the risk of server outages. The entire control is centralized, allowing you to minimize access to those critical assets. After implementing your desired policy, CHS continues to monitor your environment, alerting you on any undesired configuration drifts.