Kerberos is an authentication protocol, designed for enhanced security. Kerberos authentication protocol designed with a ticket-granting mechanism. As part of the Kerberos authentication mechanism, an Authentication Server is granting a Ticket Granting Ticket (TGT) to the client. Later in the process, the targeted server connects to a Ticket Granting Server (TGS). We recommend reading this post to better understand Kerberos’s authentication mechanism.
You can audit these two processes using this rule. Auditing Kerberos service ticket operations is important for detecting hackers trying to use Kerberos as an attack vector. Making sure Kerberos events are being tracked is part of the hardening process which can be a painful procedure. To make sure this error-prone process is not done recklessly, we recommend automating it.
CHS by CalCom automates the entire server hardening process. CHS's unique ability to 'learn' your network eliminates the need to perform lab testing while ensuring zero outages to your production environment. CHS will allow you to implement your policy directly on your production servers.
The following post will discuss:
- Kerberos Service Ticket Operations Audit
- The potential vulnerability
- Countermeasures
- Rule’s recommended and Default value
- The potential impact of configuration change
- How to configure
What is Kerberos Service Ticket Operations Audit?
This policy is recommended for Domain Controllers. By auditing Kerberos service ticket operations, you'll collect information on the events generated by Kerberos TGT and TGS activities. Auditing these events will collect and store the IP address from which the account requested TGS, when it was requested, and the encryption that was used in the process.
The following are the event log numbers:
- 4769: A Kerberos service ticket was requested.
- 4770: A Kerberos service ticket was renewed.
- 4773: A Kerberos service ticket request failed.
The Potential Vulnerability this rule tries to mitigate:
Despite being a better substitute for older authentication protocols, Kerberos still suffers from unfixable security weaknesses. Some of them take advantage of the Ticket Granting mechanism. The most iconic ones are:
The default value of this configuration is to audit only successful events. This may eventually result in missing an attack or not having enough information to investigate it.
COUNTERMEASURES:
Auditing the ticket-granting process will be useful to track and investigate security incidents.
Rule's Default and Recommended Value:
Default- Success.
Recommended- Success and Failure
The Potential Impact of Changing the Audit's Configurations:
Since this is an audit rule, there will be no direct impact on the network's function. But, it is important to build an accurate audit policy. If your audit policy is too lax, you might miss security incidents that happen in your organizations, or not have enough information to investigate them. However, if your audit policy is too severe, you might be flooded with meaningless information that will make you miss critical events such as these. In addition, gathering too much data may affect computer performance.
HOW TO CONFIGURE:
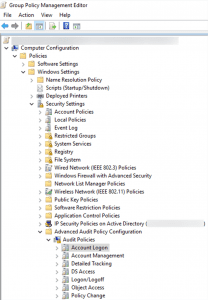
1. In the Group Policy Management Editor, go to Computer Configuration ? Policies ? Windows Settings ? Security Settings ? Advanced Audit Policy Configuration ? Audit Policies ? Account Logon.
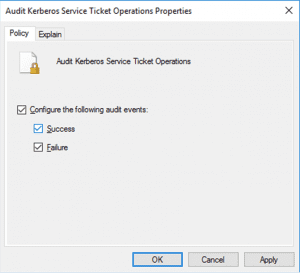
2. In the right pane, you will see a list of policies that are under Account Logon. Double-click on Audit Kerberos Service Ticket Operations, and check the boxes labeled Configure the following audit events: Success, and Failure.